A cybercriminal operating under the alias ‘vebxpert’ is reportedly selling unauthorized access to the customer relationship management (CRM) systems of two companies—one based in India and the other in South Africa. The listings, made on a cybercrime forum, offer detailed claims about the nature of access and the scale of data available, raising serious concerns about data security and the growing market for corporate access credentials.
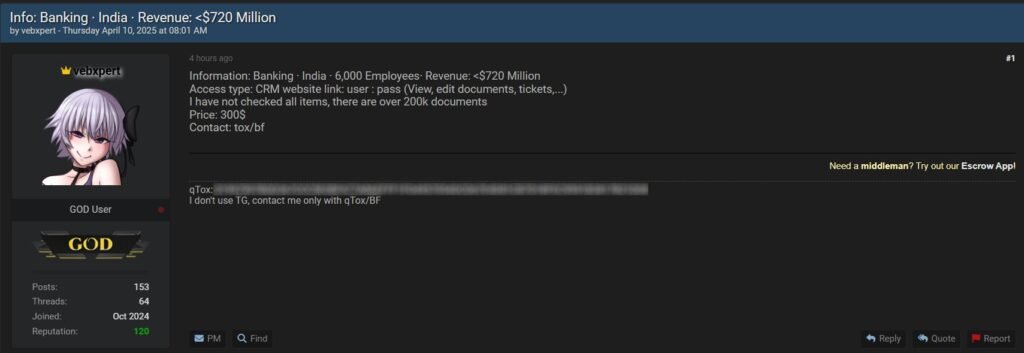
In the first case, the threat actor claims to have access to the CRM system of an Indian bank with a workforce of nearly 6,000 employees and annual revenue of less than USD 720 million, or roughly Rs 6000 crore. The listing, priced at USD 300 (around Rs 25,000), includes credentials in the format of a username and password combination that allegedly grants the ability to view and edit over 200,000 documents stored within the system.
Also Read: India’s Cyber Slaves: Meet the Men Behind Fake Profiles and Real Heartbreaks
To make the transaction more credible for potential buyers, the seller is offering escrow services—a method commonly used in cybercrime circles to reduce the risk of scams between threat actors and buyers. While the bank’s name hasn’t been revealed, and no visual proof has been shared yet, the scale of claimed access and the number of documents involved suggest that the system in question holds a significant amount of business-critical and possibly sensitive customer data.
ALSO READ: Call for Cyber Experts: Join FCRF Academy as Trainers and Course Creators
1️⃣ India – Banking Sector Access for Sale
A threat actor is selling CRM access to an Indian banking organization:
🏢 ~6,000 employees | Revenue: <$720M
🔐 Access includes: View/Edit documents, tickets
📁 Over 200k internal documents
💸 Price: $30
2️⃣ South Africa – Business… pic.twitter.com/sNyisXawnJ
— Dark Web Informer – Cyber Threat Intelligence (@DarkWebInformer) April 10, 2025
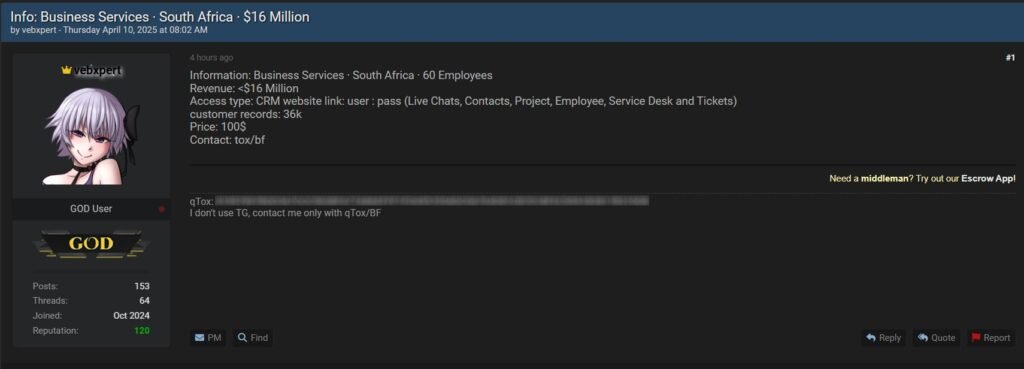
In a separate listing, ‘vebxpert’ has offered access to the CRM portal of a South African business services company. According to the post, the system contains the personal and business data of 36,000 customers. The access, priced at USD 100 (approximately Rs 8,300), includes a wide range of sensitive modules such as live chat transcripts, contact lists, project details, employee data, and information related to service desk tickets.
The actor specifies that communication for any potential deal will take place only via qTox, an encrypted peer-to-peer messaging platform favored in underground forums for its anonymity. Escrow services are also offered in this case, signaling a similar effort to assure potential buyers of the credibility of the listing.
What stands out in both cases is the absence of direct attribution. The companies’ names have not been disclosed, a tactic frequently used by threat actors to avoid drawing early attention or interference before a sale is completed. While that raises some skepticism about the legitimacy of the claims, it doesn’t eliminate the risk. In the past, similar anonymous listings have led to the exposure of real, high-profile breaches once verified by third parties. The420.in cannot independently verify the claim made by the threat actor.
Access to CRM platforms is especially dangerous because these systems act as central hubs for business operations and customer interactions. Gaining access could allow attackers to harvest sensitive data, impersonate employees, launch phishing campaigns, or even make unauthorized changes to records. In regulated industries like banking, a breach of this nature could also invite scrutiny from compliance authorities and trigger reputational damage.
With CRM systems playing such a critical role in operations, these listings act as a warning signal for businesses worldwide. Are your systems secure? Do you know who has access to your data—and how easily that access could be sold?
These questions are becoming more relevant by the day as threat actors increasingly target internal tools and platforms that many organizations still fail to secure with strong authentication, access controls, or timely updates.
The threat actor ‘vebxpert’ may have yet to provide concrete proof, but the potential fallout from such access being real is too large to ignore. Indian and South African cybersecurity teams are likely already on high alert, scanning for signs of compromise. The question now is not just who the victims are—but how many others are on the list.



