A new wave of cyberattacks is quietly spreading across global job markets, exploiting the emotional vulnerability of job seekers through malware disguised as recruitment documents. Security analysts say the campaign—powered by a remote-access trojan known as ValleyRAT—reflects an increasingly sophisticated blend of social engineering, technical deception and psychological manipulation.
Malware Masquerading as Opportunity
Cybercriminals have discovered a potent formula for infiltrating personal computers: disguise malicious software as job-related material at a time when applicants are overwhelmed with rejections, anxiety and hope. Researchers say the ValleyRAT campaign lures victims by sending emails that appear to contain candidate assessments, offer letters or onboarding documents.
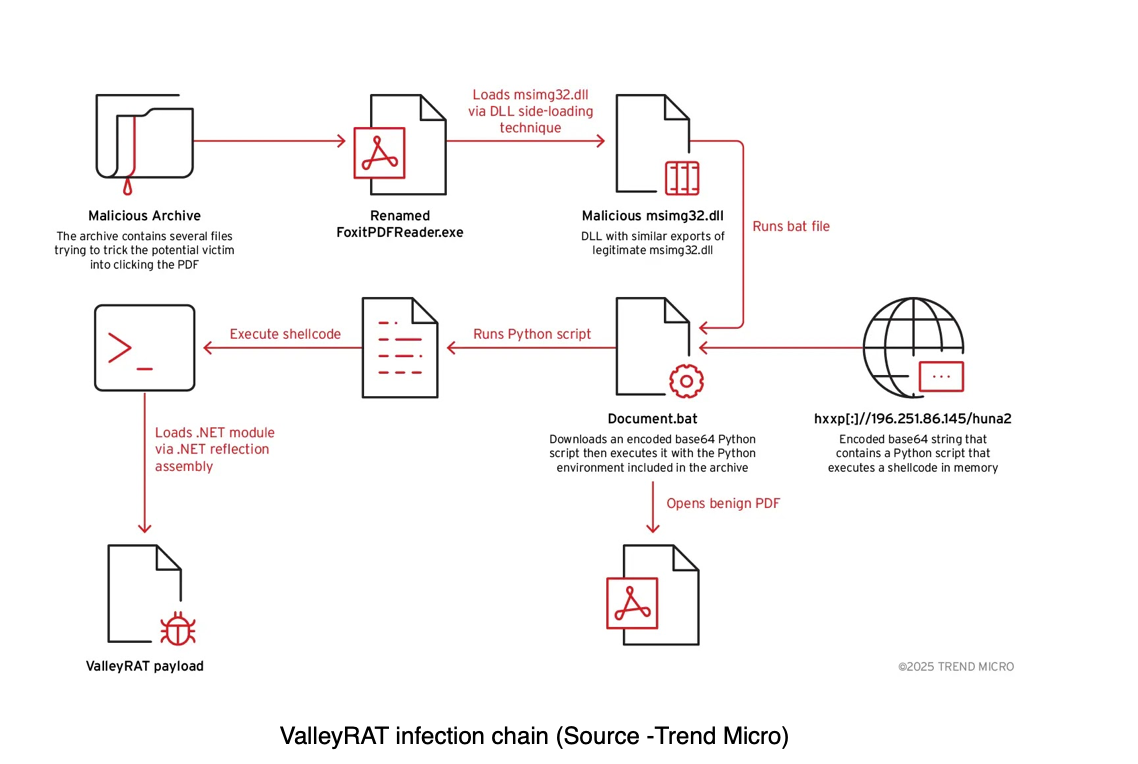
The attack begins with compressed files titled in reassuringly professional terms—Overview_of_Work_Expectations.zip or Candidate_Skills_Assessment_Test.rar. Inside, what looks like a Foxit PDF Reader icon is not a document at all but a rewritten executable. Opening the file silently loads a malicious library, triggering an infection sequence embedded deep within Windows’ search mechanisms.
Once installed, ValleyRAT grants attackers complete control over a compromised computer, monitoring activity, harvesting browser-stored credentials and extracting financial or identity-related data. Security firms warn that the malware’s persistence mechanisms allow it to survive system restarts, ensuring long-term access to sensitive information.
A Carefully Engineered Infection Chain
The technical choreography behind ValleyRAT is notably complex. Trend Micro researchers who traced the campaign uncovered a hidden Python environment embedded within the fraudulent document files. When launched, the disguised Foxit executable automatically executes a batch script that extracts the Python components, which in turn download and run the malicious payload from remote servers.
The attackers also employ DLL side-loading, a technique that exploits the way Windows prioritizes certain libraries. By placing a malicious DLL where the operating system will load it first, cybercriminals ensure the trojan activates without triggering alarms from security tools.
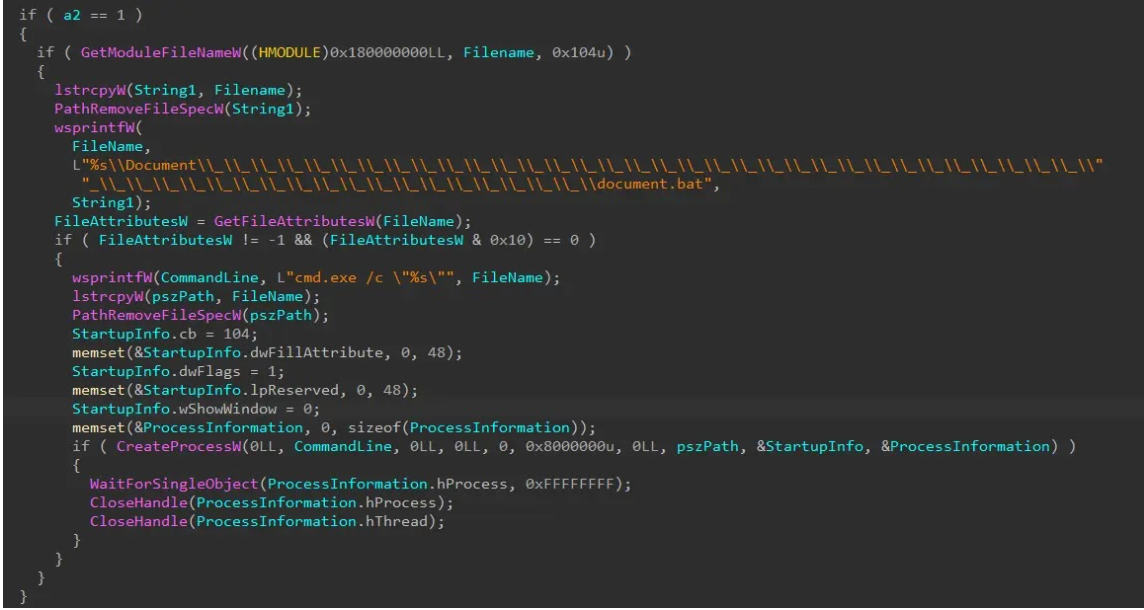
Screenshots of the underlying code reveal an elaborate set of commands designed to hide the malware within legitimate directories, execute silently and delete any visible trace of its activity. Researchers say the campaign’s success lies in its seamless blend of technical precision and human deception.
Exploiting the Emotional Strain of Job Hunting
What distinguishes the ValleyRAT campaign from traditional phishing schemes is its psychological accuracy. Job seekers—often fatigued by weeks or months of applications—are especially prone to click quickly on anything that resembles progress.
Cybercriminals rely on this emotional vulnerability. A familiar PDF logo, a polite email, a file labeled “skills assessment”—each nudges the target closer to opening the malware. Hidden directories and fake folder structures further reduce suspicion, creating a façade of normalcy even as the trojan embeds itself in the system.
Once activated, the malware operates silently while a believable job posting appears on the user’s screen, masking the intrusion until the attackers have already seized valuable credentials.
For security experts, this convergence of emotional manipulation and technical stealth reflects a broader shift in cybercrime strategy. “The human mind,” one analyst noted, “is becoming the new attack surface.”
A Rapidly Growing Threat Identified
Trend Micro first detected a notable spike in ValleyRAT activity in late October, prompting a deeper investigation into the campaign’s scope. Early indicators suggest the operation is expanding rapidly, with attackers refining both their malware architecture and their social engineering scripts to reach broader audiences beyond job seekers and HR professionals.
Evidence from infected devices shows that the malware explicitly targets login credentials stored in major web browsers—making it a direct threat to financial accounts, email platforms and identity-verification services.
Researchers warn that the campaign is far from over. Its modular design allows operators to deploy additional payloads, pivot to new targets or repurpose the infrastructure for unrelated attacks. As unemployment fluctuations and economic uncertainty persist, experts fear that job-seeking populations will remain a lucrative and vulnerable target.



