Fake CoWIN Fraudster had taken down its Onion Server after briefly publishing this on Darknet on June 10, owing to great pressure
Our Observations and Finding:
The same entity has tried to bring another onion site this time in Deep Web, with the following screenshot on11th June. However this time they didn’t claim CoWIN data, rather they put it as ‘Database Covid19 Vaccination from India“
ALSO READ: CoWIN Hack Decoded: Fake News Exposed
Going by the pattern, our observation points, this is being done by a mediocre hacker. Here one has to pay first, once payment is done, a code gets generated which needs to be pasted for downloading the data.

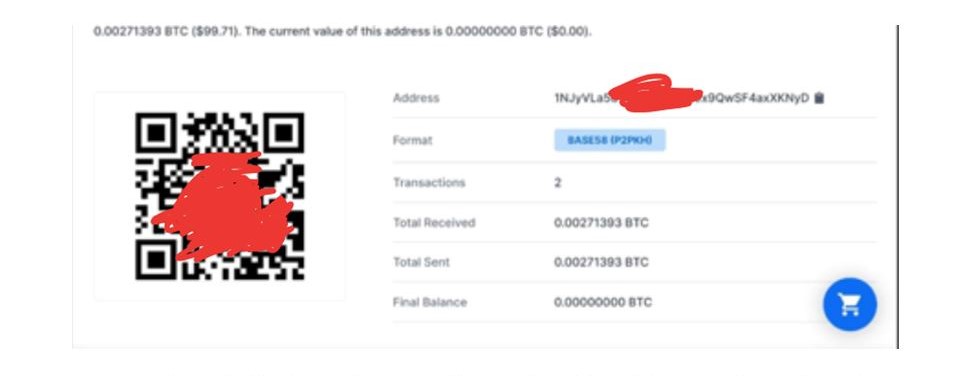
We could identify the Wallet Address which was being used to collect the payment for this sale of data.

There is no recent transaction in this wallet, which points that no one has purchased this data till now. The last transaction was on 21st May 2021: One Credit & One Debit of 0.00271393 BTC which was equivalent to US$99.71.
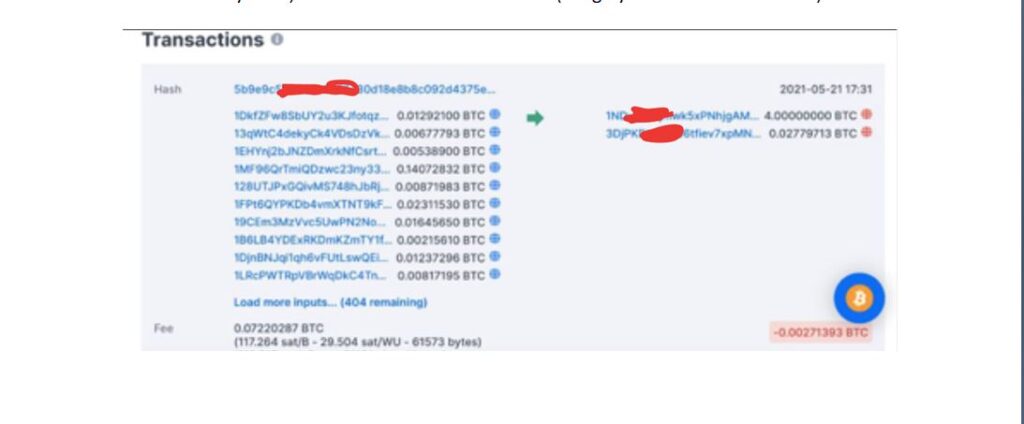
Interestingly on the further probe, we could trace the wallet of the entity, from where this reseller might have procured the original data. This wallet owner could either be the actual owner of data or a BitCoin trader. Quite a few transactions have taken place in this wallet & as of 21st May 2021, it contained 4.002779713 BTC (roughly translated to Rs.1 Cr +)
Further Actions
More importantly with these inputs, even “Sink Holes” can also be identified, where BitCoin gets converted into Real Currency.
Our scope is limited to Tracking & Tracing Cyber Fraud. With the above input, Law Enforcement Agencies can seize/confiscate, flush the wallet under the prevailing Law of land.
Area of Concern: Apart from other use cases, Owing to the Accuracy of these data sets, even “Good Companies” try to source these databases, which assists them in launching a precise marketing campaign. Even they are getting duped with these menaces.
Key Take Away: The above case study shows the positive impact & advantage of having the RED TEAM exercise, where Cyber Fraudsters/Attackers are chased back quickly & put on the back foot. This concept has derived from the phrase “Diamond cuts Diamond”. The organizations may wish to include this strategy in their Cyber Defense Plan, at least they would be able to defer their imminent attacks
Case Study by: RED Team of Armantec, led by Shamsher Bahadur – Cyber Security Practice Head.
This Article has been Submitted by Armantec Systems Pvt Ltd (www.armantecsystems.com), a Noida Based Threat Intelligence & RED Teaming Consulting Firm, with the prime focus on custom Ransomware Attacks Solution for Critical Information Infrastructures (CIIs).
Follow The420.in on Facebook, Twitter, LinkedIn, Instagram, YouTube & Telegram


