A newly uncovered phishing campaign, dubbed PhantomCaptcha, has revealed a complex web of fake domains, weaponized PDFs, and WebSocket-powered malware — an operation that cybersecurity analysts say demonstrates an unusually high level of planning and tradecraft
A Precision Strike on Humanitarian Networks
Cybersecurity researchers at SentinelOne have disclosed details of a coordinated spear-phishing campaign targeting humanitarian and governmental organizations linked to Ukraine’s war relief operations.
On October 8, 2025, individual members of groups such as the International Red Cross, UNICEF’s Ukraine office, the Norwegian Refugee Council, and regional Ukrainian administrations across Donetsk, Dnipropetrovsk, Poltava, and Mikolaevsk were targeted. The operation, codenamed PhantomCaptcha, deployed weaponized PDF attachments posing as official correspondence from the Ukrainian President’s Office.
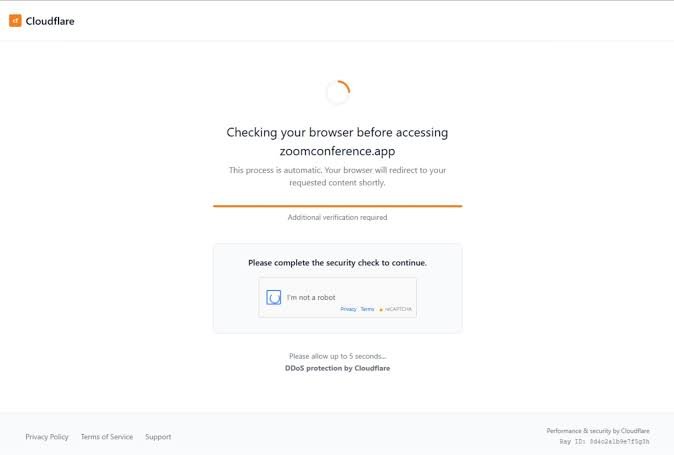
When opened, these PDFs contained embedded links that redirected victims to a counterfeit Zoom site — zoomconference[.]app — engineered to execute malicious PowerShell commands through a ClickFix-style fake CAPTCHA page, mimicking a browser security check.
SentinelOne described the campaign as one of the most disciplined operations seen since the onset of the Ukraine war, with the threat actors exhibiting “sophisticated planning and strong commitment to operational security.”
The Mechanics of Deception
At the heart of PhantomCaptcha is a layered attack chain designed to bypass conventional detection systems. The bogus Cloudflare verification page acts as a mediator, establishing a WebSocket connection with an attacker-controlled server and generating a JavaScript-based client ID. If validated, victims were seamlessly redirected to a legitimate, password-protected Zoom meeting — a ruse meant to enhance authenticity.
Researchers suspect that this mechanism may have been used for live social engineering calls, though SentinelOne did not directly observe such events during its investigation. Once the malicious command was executed, an obfuscated downloader retrieved a second-stage payload from a remote server, initiating reconnaissance of the compromised host.
The final payload, identified as a WebSocket-based Remote Access Trojan (RAT), was hosted on Russian-owned infrastructure and allowed arbitrary command execution, data exfiltration, and the potential deployment of additional malware.
FCRF Launches CCLP Program to Train India’s Next Generation of Cyber Law Practitioners
Infrastructure, Targets, and Attribution Clues
Technical evidence points to a carefully orchestrated infrastructure lifecycle. Preparations reportedly began on March 27, 2025, with the registration of goodhillsenterprise[.]com — a domain later used to distribute obfuscated PowerShell scripts. Another related domain, zoomconference[.]app, was active for only a single day on October 8, coinciding precisely with the attack window.
VirusTotal submissions indicate that the eight-page weaponized PDF was uploaded from multiple countries, including Ukraine, India, Italy, and Slovakia, suggesting broad targeting.
The malware communicated with a remote WebSocket server hosted at wss://bsnowcommunications[.]com:80, transmitting Base64-encoded JSON messages that allowed remote command execution via PowerShell.
While SentinelOne has not attributed the operation to any confirmed group, aspects of its tooling and domain management overlap with patterns seen in operations by COLDRIVER, a Russia-linked hacking group known for targeting European political and humanitarian entities
The Phantom Behind the Code
Analysts say PhantomCaptcha reflects a high-caliber adversary with extensive operational discipline. SentinelOne characterized the group as “highly capable,” citing compartmentalized infrastructure, deliberate exposure control, and a six-month gap between setup and activation — a hallmark of professional intelligence operations.
Following each wave of attacks, the operators swiftly dismantled user-facing domains while maintaining backend command-and-control capabilities — an indicator of technical maturity and a deep understanding of both offensive and defensive cyber tactics.
The campaign also deployed Android-based fake apps hosted on princess-mens[.]click, designed to collect geolocation data, call logs, media files, and other sensitive information from compromised devices.