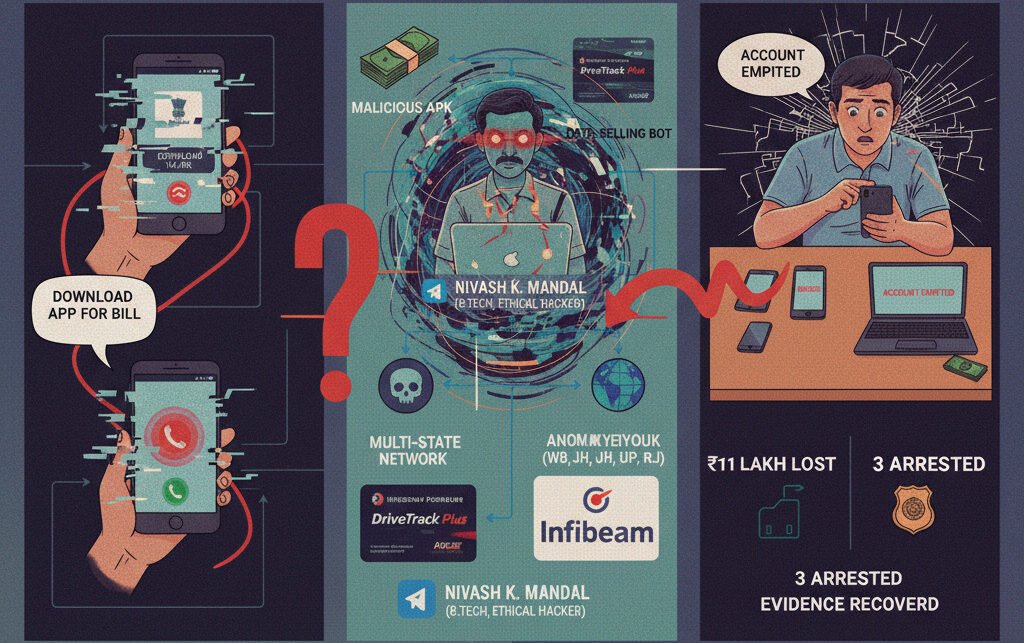
NEW DELHI — Delhi Police say they have broken a major cyber-fraud network that blended social engineering, malware-driven fund theft, and a multilayered digital laundering system across several states.
The operation culminated in the arrest of three accused, including the alleged mastermind, identified as Nivash Kumar Mandal, who police say ran a Telegram channel named “Baba Kismatwale.” Authorities also detained a minor who allegedly conducted phone calls impersonating officials to lure victims.
Investigators revealed the gang posed as representatives from the Delhi Jal Board, banks, and private power distributor BSES. Calls would direct targets to download a fake government-linked APK file — “Delhi Jal Board V4.apk” — through which victims unknowingly handed over banking credentials.
Shortly after installation, police said, accounts were drained in real time.
Layering Money Through Fuel Cards and Payment Gateways
What began with fraudulent calls evolved into a financial pipeline engineered for concealment. According to investigators, stolen funds were routed through Hindustan Petroleum’s DriveTrack Plus cards, a corporate fleet card platform designed for fuel payments, not criminal laundering.
From there, police allege the money moved through multiple banking channels and the Infibeam payment gateway, part of a wider layering strategy to evade tracing.
Officers recovered nine mobile phones, ATM cards, three chequebooks, a MacBook, an iPad, and ₹47,800 in cash. One complainant alone reportedly lost ₹2 lakh through the malicious app.
Jamtara’s Shadow and a Technocrat at the Center
Police say the alleged ringleader is not a typical cyber-fraud foot soldier. Mandal holds a B.Tech degree and a certificate in ethical hacking, and is named in four previous cybercrime cases. In 2024, he reportedly created a Telegram bot selling bank-customer data to fraudsters — illustrating how black-market data pipelines now blend automation with deception.
His associate, Pradyumn Kumar Mandal, arrested from Jamtara — long notorious as India’s phishing hub — has prior cases too. The minor associate allegedly handled victim calls, mimicking authority with practiced precision.
The gang reportedly operated across West Bengal, Jharkhand, Uttar Pradesh, and Rajasthan, highlighting the geographic sprawl of modern cyber syndicates.
A Playbook of Social Engineering and Digital Sophistication
While Jamtara fraud has historically leaned on basic identity theft and phishing calls, this case signals escalation. Fraudsters are now deploying:
Customized malicious APKs
Corporate fuel card routing
Payment-gateway layering
Telegram-based data-selling bots
Credential harvesting via fake public-utility personas
Cybercrime officials say the case marks a shift in tactics — blending grassroots scam techniques with fintech-grade laundering.
Delhi Police continue to trace additional members, as investigators warn that youth with legitimate tech skills entering the cyber underground represent an emerging security challenge.