China’s cyber espionage operations have reached unprecedented levels, with a staggering 150% surge observed in 2024, according to CrowdStrike’s 2025 Global Threat Report, released on February 27, 2025. This escalation, coupled with a 300% spike in attacks targeting critical industries, highlights the growing sophistication and aggression of Chinese-backed hacking groups.
The most heavily targeted sectors were finance, media, and manufacturing.
CrowdStrike identified seven new China-linked adversaries in 2024 and successfully blocked more than 330 cyber intrusion attempts attributed to these groups.
Adam Meyers, Head of Counter-Adversary Operations at CrowdStrike, warned, “China’s increasingly aggressive cyber espionage, combined with the rapid weaponization of AI-powered deception, is forcing organizations to rethink their approach to security.”
Nominations are open for Honouring Women in Cyberspace on International Women’s Day 2025- Nominate Now!
CrowdStrike’s Observed Cyber Threat Trends in 2024
Other key cyber threat trends identified in the report include:
- Voice phishing (vishing) skyrockets – Attacks surged by 442% between the first and second half of 2024.
- Malware-free attacks dominate – 79% of detected intrusions were malware-free, up from 75% in 2023 and just 40% in 2019. Additionally, access broker advertisements on the dark web increased by 50% in 2024.
- Vulnerability exploits rise – 52% of vulnerabilities observed in 2024 were linked to initial access, with hackers increasingly leveraging chained exploits for greater impact.
- Cloud environments under attack – Cloud intrusions rose 26% in 2024, with valid account abuse accounting for 35% of incidents in the first half of the year.
- North Korean hackers embrace insider threats – 40% of cyber incidents involving North Korea’s adversary, Famous Chollima, relied on insider schemes, including IT worker infiltration.
- Breakout time accelerates – The average time from initial access to intrusion dropped to 48 minutes in 2024, down from 62 minutes in 2023. The fastest breakout time recorded was just 51 seconds.
- Generative AI (GenAI) fuels cybercrime – While mostly used for advanced social engineering tactics, some nation-state actors—particularly from Iran—used GenAI for vulnerability research and exploitation.
During a press briefing on February 25, Meyers stated, “We called this report ‘The Year of the Enterprising Adversary’ because we have seen threat actors mature significantly. They have figured out new ways to gain access and evade modern security tools.”
CrowdStrike’s Global Threat Report in Numbers
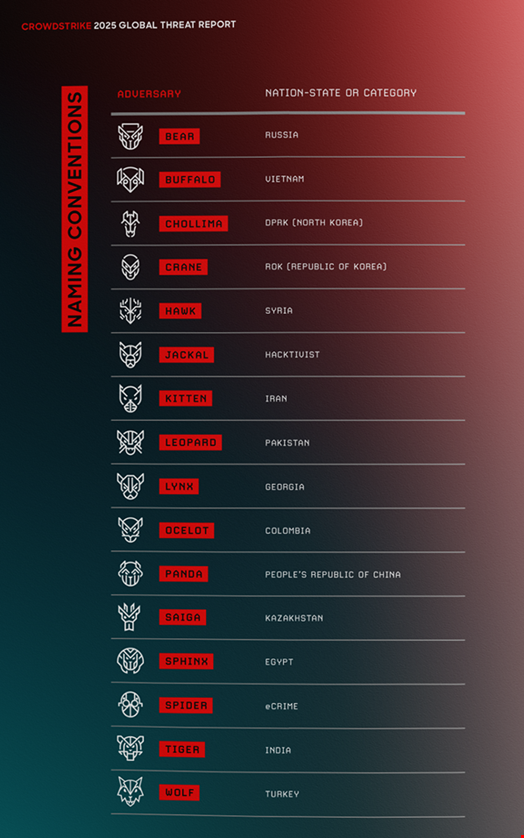
In its 13th Global Threat Report, CrowdStrike tracked 257 adversaries worldwide, with 26 new threat actors emerging in 2024. The company also detected over 140 activity clusters—malicious operations with unknown attribution.
Additionally, CrowdStrike identified two new nation-state threat actors:
- Egypt – Tracked as ‘Sphinx’
- Kazakhstan – Tracked as ‘Saiga’
“Seeing more nations deploying cyber intrusions and espionage operations is a significant concern,” Meyers concluded.
SOURCE: SOCIAL MEDIA


