NEW DELHI: A cross-border fraud network operating through Telegram is targeting Indian users with fake online review jobs, leading to financial losses running into crores of rupees.
A detailed investigation by HackElite, a cybersecurity research and investigation team, has traced the operation to Pakistan and revealed how organised scam groups are using automation tools, masked digital infrastructure, and social engineering to exploit victims across India
HackElite’s investigation shows that the scam typically begins with an unsolicited message on Telegram. The sender offers easy part-time work that promises quick income for rating hotels or movies online. The task appears harmless and requires no experience. In many cases documented by HackElite, victims receive a small payment for an initial assignment, which creates trust and makes the opportunity appear legitimate.
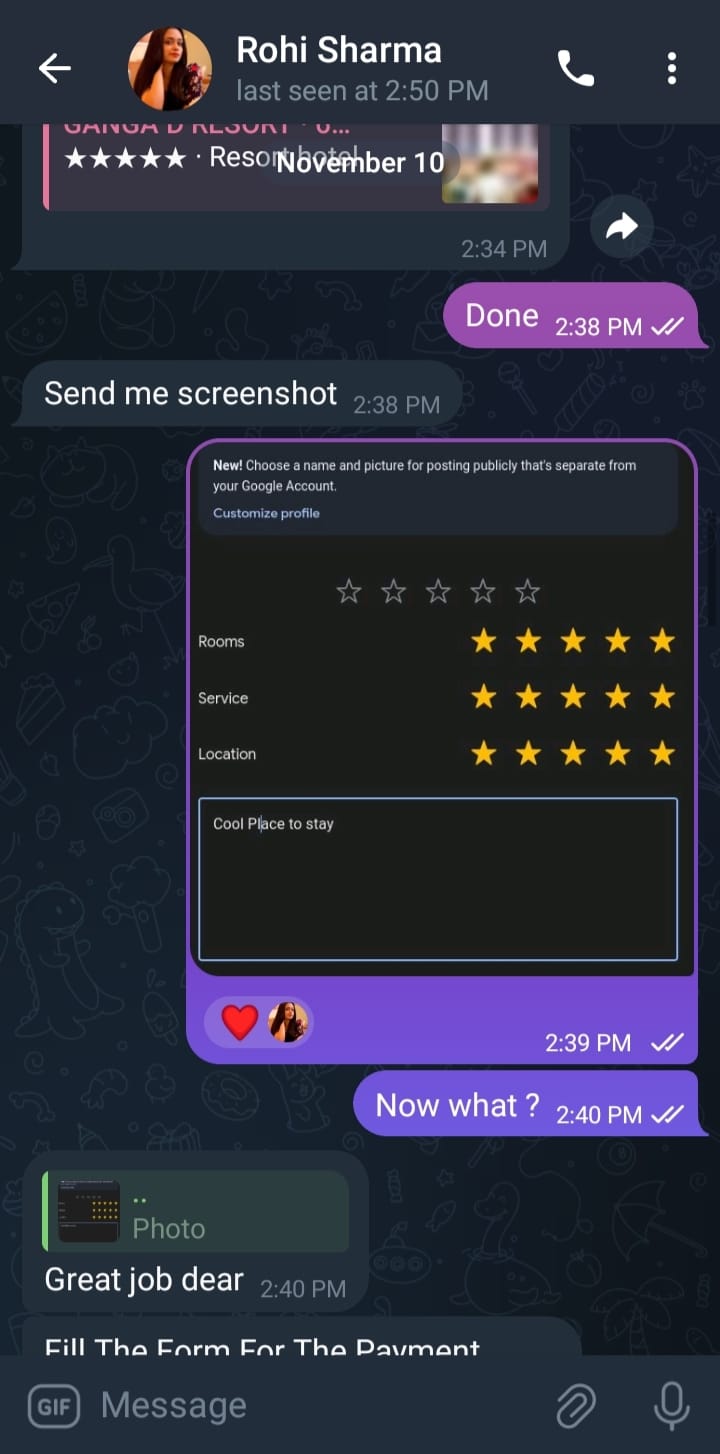
According to HackElite, the fraud unfolds in carefully planned stages. After the first contact, victims are asked to complete a so-called demo task. This involves clicking a link, selecting a hotel or movie listing on Google Maps, posting a five-star review, and sharing a screenshot as proof. HackElite notes that this step serves multiple purposes. It confirms the victim’s willingness to cooperate and creates artificial legitimacy around the job offer.
Once the demo task is marked complete, researchers observed that scammers quickly shift focus to collecting financial information. Victims are asked for bank account details, UPI IDs, and preferred payment methods. This marks the transition from deception to direct financial fraud. The analysis shows that this request is often framed as a routine step for releasing payments.
The next phase, HackElite says, is where most victims suffer heavy losses. Scammers introduce artificial limits on daily reviews and claim higher earnings are possible only through paid reviewer plans. These plans typically include a Silver Plan costing Rs 5,000 for 100 reviews and a Gold Plan costing Rs 10,000 for 200 reviews.
HackElite found that victims who pay for these plans receive no meaningful income. Instead, they are asked to pay additional amounts for activation charges, taxes, or verification fees. When victims stop paying, they are blocked and removed from all communication channels.
Investigation makes it clear that this is not the work of isolated individuals. Researchers traced the operation to the use of WorkGram, a cloud-based Telegram automation platform. HackElite found that the tool enables bulk messaging, multi-account management, automated replies, and outreach without physical SIM cards. These features allow scammers to contact thousands of Telegram users daily, indicating a structured and scalable fraud operation.
ALSO READ: Padma Bhushan Scientist T. Ramasami Loses ₹57 Lakh in Digital Arrest Scam
The infrastructure behind the scam also raised red flags. HackElite examined shortened links shared with victims for demo tasks, including the domain teach.link. The investigation found that the domain’s ownership details were fully redacted, with historical records linking it to a China-based registrant. The domain remains active until February 2026. HackElite notes that such links are commonly used to track user activity while concealing the final destination, making enforcement action more difficult.
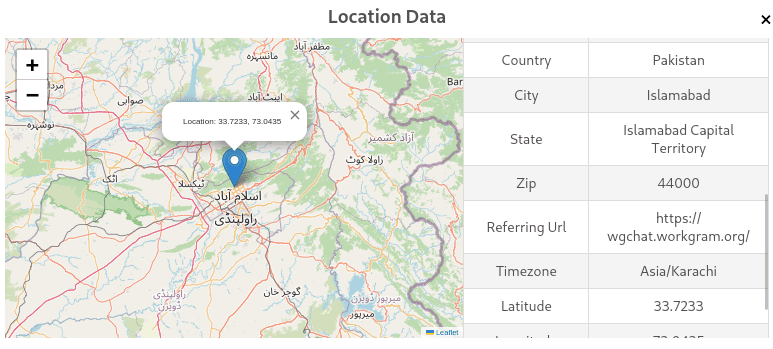
To identify the operators’ location, researchers conducted a controlled engagement with the scammer. During this operation, researchers persuaded the scammer to click on an IP-logging link. The captured metadata showed the access originated from Islamabad, Pakistan, using a Windows desktop system and the Chrome browser. The referrer URL pointed directly to WorkGram’s dashboard. HackElite assessed these findings as strong evidence of an organised, Pakistan-based operation rather than a lone actor.
Throughout its investigation, HackElite identified recurring warning signs. These include job offers made only through Telegram, early requests for banking or UPI details, demands for upfront payments to earn money, promises of guaranteed or unusually high returns, and persistent pressure to act quickly. HackElite emphasises that legitimate employers do not ask jobseekers to pay in advance for work.
Researchers advises users who receive such messages to stop all communication immediately, block and report the Telegram account, and avoid sharing any financial information. Those who have already shared details are urged to contact their bank’s fraud department without delay. Complaints can be filed through the national cybercrime helpline 1930 or on the National Cybercrime Reporting Portal at cybercrime.gov.in.
The findings from HackElite underline how online job scams have evolved into organised, cross-border fraud operations that combine automation with psychological manipulation. What begins as a message promising easy income can quickly turn into a carefully managed process designed to extract large sums of money from unsuspecting users.



