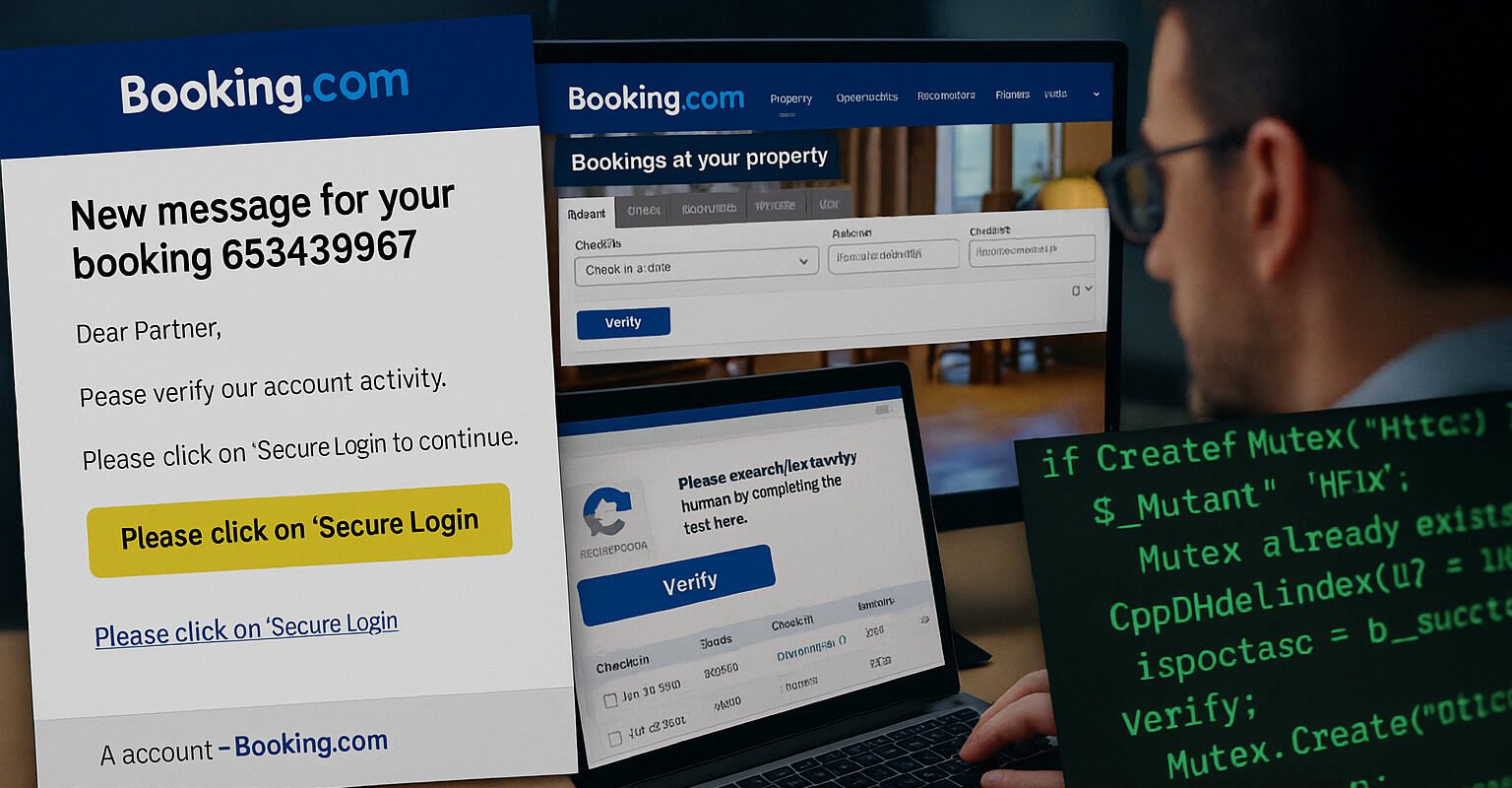
Cybersecurity researchers have uncovered a large-scale phishing campaign targeting hotel systems across the globe, in which cybercriminals impersonate Booking.com and other travel platforms to deploy the PureRAT malware.
The campaign, analyzed by French cybersecurity firm Sekoia, uses a deceptive technique known as “ClickFix”, which manipulates hotel staff into following seemingly legitimate “security verification” steps that secretly compromise their computers.
“This campaign uses compromised business email accounts to send phishing messages to hotel establishments worldwide,” Sekoia said. “By impersonating Booking.com, the attackers redirect victims to fake reCAPTCHA pages that execute malicious scripts, ultimately installing PureRAT.”
How the ClickFix Trap Works
The phishing emails often appear authentic — sent from legitimate, previously compromised hotel accounts. Recipients are told to click a verification link for account security.
Clicking the link redirects them through several pages designed to look like a reCAPTCHA security check. The pages then instruct the victim to run a PowerShell command, disguised as a technical verification step.
Once executed, this command downloads a malicious ZIP archive containing a DLL file that uses side-loading to install PureRAT (also known as zgRAT) — a modular remote access trojan with capabilities such as:
-
Keystroke logging
-
Webcam and microphone control
-
File upload/download
-
Network proxying and persistence through registry keys
Researchers noted that the attackers’ infrastructure cleverly switches users from HTTPS to HTTP mid-session to bypass browser safeguards and facilitate the malware drop.
From Hotel Admins to Guests: A Double-Fraud Chain
The ultimate goal of the campaign is to steal administrator credentials from hotel booking platforms like Booking.com, Expedia, Airbnb, and Agoda. These stolen credentials are then sold on dark web forums or used to carry out secondary scams targeting hotel guests.
In several cases, threat actors used the stolen credentials to contact guests directly — via email or WhatsApp — claiming there was an issue with their booking. Victims were asked to “verify” their payment information on cloned websites that mimic the official platforms, leading to large-scale credit card theft.
Cybercriminals are reportedly sourcing information about hotel administrators from criminal marketplaces like LolzTeam, even offering profit-sharing schemes to those who can supply valid Booking.com credentials.
“Booking.com extranet accounts are now a lucrative black-market commodity,” Sekoia said. “Attackers sell these as cookies or credential pairs obtained from infostealer logs, making them vital assets in the cybercrime economy.”
Cybercrime as a Service
Investigators have identified an emerging “fraud-as-a-service” ecosystem supporting these operations. A Telegram bot — operated by a user called “moderator_booking” — was found advertising bulk purchases of Booking.com, Expedia, and Agoda logs, claiming to manually verify them within 48 hours.
Verification is performed using log checker tools, available for as little as $40, which test whether stolen credentials are still valid by authenticating them through proxy servers.
“This reflects the professionalization of the cybercrime model,” Sekoia noted. “Every step — from phishing to data resale — is now modular, scalable, and automated.”
The Evolution of ClickFix: Smarter, Faster, More Convincing
A report by Push Security adds that recent versions of ClickFix phishing pages have become even more deceptive. They now include:
-
Embedded demonstration videos showing how to “verify” security steps
-
Countdown timers and activity counters that simulate real-time traffic (“153 users verified this hour”)
-
OS-adaptive instructions, telling Windows users to open “Run” or Mac users to open “Terminal”
-
Clipboard hijacking, which automatically copies malicious code to the victim’s clipboard
“ClickFix pages are evolving rapidly,” Push Security warned. “By combining behavioral psychology and technical sophistication, attackers are dramatically increasing success rates while evading traditional email filters.”
A Growing Threat to the Travel Ecosystem
The hospitality sector, which relies heavily on third-party booking and payment platforms, has become an ideal target for credential theft and lateral fraud. Analysts warn that such attacks could disrupt not just hotels, but entire tourism supply chains — from reservation systems to guest communications.
“The professionalization of cybercrime in this sector underscores the need for layered defenses,” said one European cybersecurity analyst. “Hotels are no longer dealing with amateurs; they’re up against organized, revenue-driven threat actors.”