Dehradun: An emerging Android malware disguised as an official e-challan is exploiting trust between contacts — and exposing a new frontier of social engineering.
The Bait: A Familiar Message With a Hidden Threat
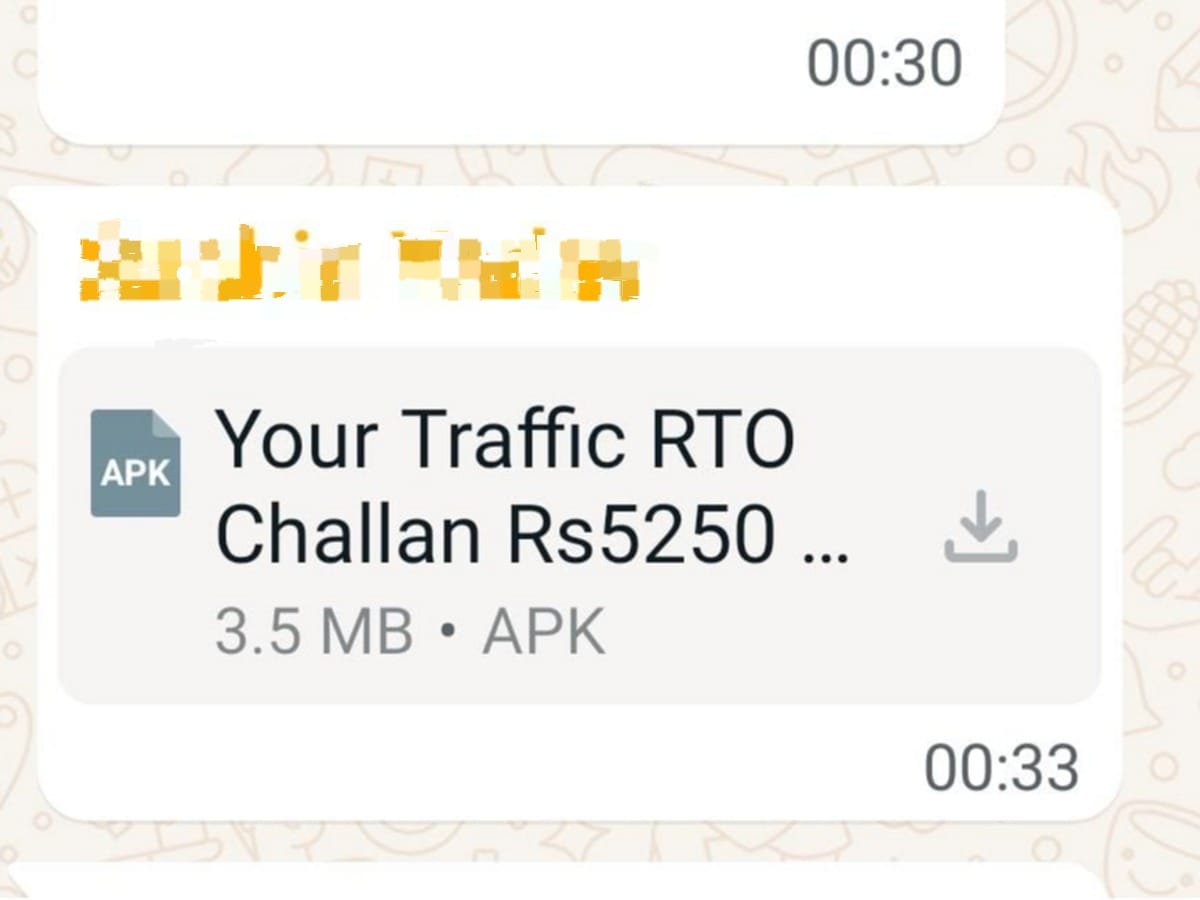
It begins innocuously enough — a WhatsApp message from a known contact, bearing a file labeled “RTO e-Challan.apk.” For many recipients, the name evokes an image of bureaucratic normalcy, perhaps a traffic fine notification. But for dozens of users in Dehradun, that file proved to be a digital Trojan horse.
State cybercrime units have issued warnings after more than twenty residents reported their WhatsApp accounts — and in some cases, their bank credentials — being compromised. Investigators say the so-called RTO Challan APK scam marks a troubling shift attackers are now weaponizing ordinary, trusted communication channels rather than relying on suspicious links or emails.
“The file often appears to come from someone you know,” said Navneet Singh, senior superintendent of police and head of the state’s cybercrime division. “That familiarity is what lowers defenses.”
Inside the Infection: How the APK Takes Over
Unlike conventional phishing links, the malicious APK file requires the user to manually install it — a step Android systems typically warn against. Once installed, it grants the attacker remote access to the device, capturing WhatsApp data, chat histories, and sensitive financial information.
Essentially, the malware acts as a gateway, handing over control of the victim’s WhatsApp account to hackers. They can then read private conversations, impersonate the user, and spread the infection to others through new messages.
“The malware is quirky,” explained a cyber-forensics expert involved in the investigation. “It targets only Android devices. iPhones are safe because APK files can’t run outside the Android environment.”
One user, Arun Kumar, narrowly avoided infection when he opened the same file on his iPhone — the malicious payload failed to execute.
The First Firm to Assess Your DFIR Capability Maturity and Provide DFIR as a Service (DFIRaaS)
The Human Cost of Digital Trust
For victims like Vinod, a restaurant owner from Dehradun, the damage extended beyond embarrassment. “Because I knew the person, I just opened it without thinking,” he recalled. Within hours, his WhatsApp logged him out. Soon after, he began receiving banking OTPs — a signal that hackers were attempting to breach his financial accounts.
Such stories underscore how cybercriminals are exploiting the psychology of trust, particularly in social messaging environments. A seemingly harmless exchange between friends or colleagues now doubles as a potential attack vector.
Singh urged users not to open unsolicited files on WhatsApp — even if sent by familiar contacts — and to enable two-step verification. “Trust is being weaponized,” he said. “The next attack doesn’t always come from a stranger.”
The Larger Shift: From Phishing Links to Mobile Payloads
Security experts say the RTO Challan scam reflects a broader evolution in mobile cybercrime. Attackers are moving away from crude phishing campaigns toward payload-based attacks — malicious code hidden in files that appear legitimate.
These APK-based intrusions are harder to detect, more persistent, and rely on users’ habits of sharing and downloading content.
“It’s an emerging paradigm,” a senior cybersecurity researcher noted. “Fraudsters no longer need to build fake websites; they just need one errant tap.”
Authorities recommend keeping Android devices locked to Play Store downloads, verifying any unexpected file before installation, and reporting incidents promptly to local police or the national cybercrime portal.
“In cybersecurity,” the expert added, “trust has become both the target and the weapon.”