Security researchers have uncovered one of the largest coordinated malware operations on YouTube, using fake tutorial videos and hijacked channels to spread information-stealing software across the internet.
A Hidden Epidemic of “How-To” Malware
In a finding that has sent ripples through the cybersecurity community, researchers at Check Point have traced a sprawling malware campaign—nicknamed the YouTube Ghost Network—that has quietly operated for years, exploiting the very platform where millions go to learn and create.
The operation, which investigators describe as one of the largest of its kind, leverages thousands of YouTube videos disguised as software tutorials. These clips promise free or “cracked” versions of premium tools like Adobe Photoshop, FL Studio, and Microsoft Office, alongside cheats for popular games such as Roblox. One compromised channel alone—boasting 129,000 subscribers—pushed a fake Photoshop crack that drew nearly 291,000 views.
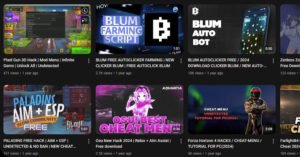
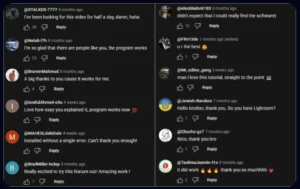
Each video follows a nearly identical script: a persuasive walkthrough leading viewers to download password-protected archives via Google Drive or Dropbox. Comments supply the password and glowing “user reviews,” lending a false sense of legitimacy. The catch? The ZIP or RAR file carries stealer malware, a class of malicious software built to harvest browser passwords, session cookies, cryptocurrency wallets, and even corporate logins.
The Mechanics of the Ghost Network
According to Check Point’s analysis, more than 3,000 interconnected videos form the campaign’s backbone. The network’s structure is modular—designed to survive takedowns and evolve quickly. Hijacked YouTube accounts upload the videos, while separate personas manage comments, pinned messages, and community interactions. External file-hosting sites deliver the infected payloads.
The malware strains observed, including Rhadamanthys and Lumma, are known information stealers. Once executed, they silently collect sensitive data that can bypass even multi-factor authentication (MFA) through stolen session cookies. From there, attackers can drain funds, compromise developer portals, and pivot into larger corporate systems.
Researchers describe the network’s adaptability as “industrial.” When one channel or link is banned, new ones appear—mirroring tactics seen on GitHub, Telegram, and other underground ecosystems. Paid ad campaigns and keyword optimization have even been used to push these videos higher in YouTube’s algorithm, expanding their reach beyond organic discovery
The Business of Stealer-as-a-Service
Behind the operation lies a thriving criminal economy. “Stealer-as-a-service” models allow affiliates to rent malware builders for a subscription fee, generating unique variants to evade detection. The stolen data—ranging from credentials and crypto keys to entire browser sessions—flows into searchable logs sold on underground markets.
These logs are highly lucrative. A single set of credentials can unlock multiple online accounts, while session cookies can bypass passwords entirely. Experts warn that once a device is infected, the fallout can be both personal and professional: a compromised YouTube account may lead to stolen email sessions, drained crypto wallets, or access to corporate intranets.
The scale of the operation, coupled with its persistence, has drawn comparisons to ransomware networks in its sophistication and profit-driven organization.
The First Firm to Assess Your DFIR Capability Maturity and Provide DFIR as a Service (DFIRaaS)
Protecting Yourself from the Trap
Security experts say awareness is the strongest defense. Videos offering free or cracked software, premium plugins, or keygens should be treated as immediate red flags—especially if they instruct viewers to disable antivirus tools like Windows Defender.
Users are advised to download only from verified vendors, scan unknown files in a sandbox environment or non-admin account, and enable multi-factor authentication—preferably with hardware keys. Compromised users should disconnect infected devices, change passwords from a clean system, revoke all app tokens, and migrate cryptocurrency funds to fresh wallets.
Creators and advertisers aren’t immune either. YouTube channels should enforce strict access controls, monitor uploads for anomalies, and audit permissions for brand managers and editors. Advertisers, meanwhile, are urged to review campaigns to avoid inadvertently funding malicious content.
As one researcher summarized:
“This is no longer about isolated hackers—it’s about professionalized cybercrime embedded within everyday internet behavior.”