NEW DELHI: A new ransomware has been discovered in India that forces victims to donate new clothes to the destitute, feed children in popular pizza restaurants, and provide financial assistance to anyone who requires urgent medical attention but cannot afford it, claims Bengaluru based cyber security firm – CloudSEK.
CloudSEK researchers also cautioned that the Goodwill ransomware might also cause temporary, and possibly permanent, data loss, as well as a possible shutdown of the organization’s activities and income loss.
According to the new study, CloudSEK researchers discovered GoodWill malware in March 2022. As the threat group’s name suggests, the operators are reportedly motivated by social justice rather than traditional financial gain.
ALSO READ: Cyber Attack On India’s Biggest Port: Ransomware Cripples Services At Jawaharlal Nehru Port Trust
Once infected, the GoodWill ransomware infection encrypts documents, images, movies, databases, and other essential assets, rendering them unavailable unless the decryption key is provided.
In exchange for the decryption key, the actors suggest that victims perform three socially motivated activities: donate new clothes to the homeless, record the action, and post it on social media, take five less fortunate children to Dominos Pizza Hut or KFC for a treat, take pictures and videos, and post them on social media, and provide financial assistance to anyone who needs urgent medical attention but cannot afford it, at a nearby hospital, record audio, and share it with the actors, the study said.
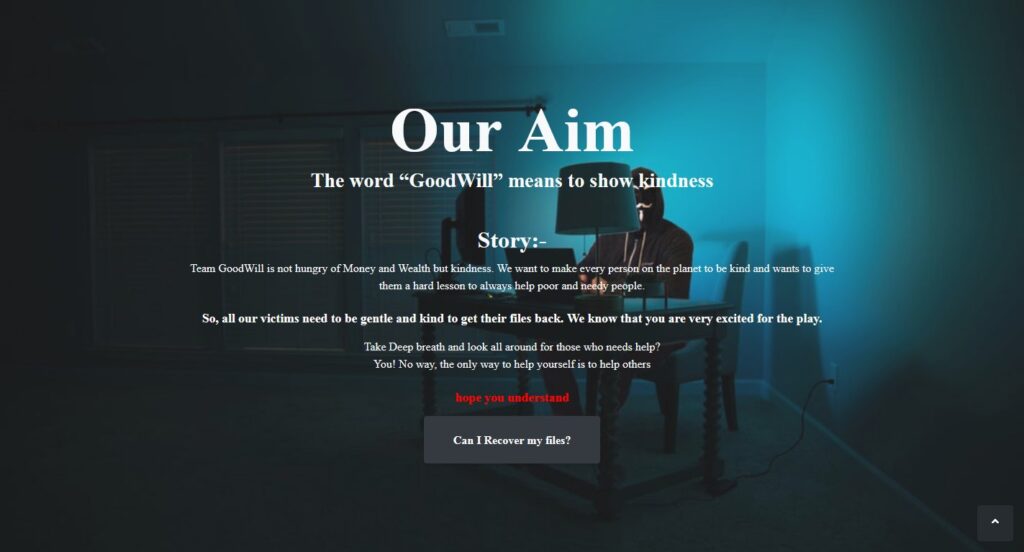
After completing all three acts, the ransomware requests that victims post a note on social media (Facebook or Instagram) about “how you turned yourself into a good human being by becoming a victim of a ransomware called GoodWill.” After performing all three operations, the ransomware operators validate the victim’s media files and social media posts.
According to the allegation, the actor will subsequently distribute the entire decryption kit, which contains the main decryption tool, password file, and video lesson on how to retrieve all crucial files.
“Our researchers were able to trace the ransomware group’s email address back to an India-based IT security solutions & services organisation that provides end-to-end managed security services,” according to the report.
Follow The420.in on
Telegram | Facebook | Twitter | LinkedIn | Instagram | YouTube



