We have heard about Phishing for the last decade or more. As technology advances and people were getting educated about Phishing, how not to fall prey to Phishing, how 2FA (2Factor Authentication) or MFA (Multifactor Authentication) helps them to maintain their Cyber Security. Well, Cyber Attackers have also advanced themselves and now they have come out with a concept of “Consent Phishing”. Using this concept, normal users can be tricked very easily and all 2FA and MFA mechanisms shall get bypassed. Time to buckle up to address this!
Concept of Consent Phishing: This methodology bypasses the existing traditional methods, which organizations have been taught to adopt till now to wane of Phishing Attacks, by deploying F2A, MFA.
Use Case: Let’s assume, An user from Finance Department is browsing his/her emails after the weekend & trying to clear the backlog of emails and come across with following email, which talks about Financial Report.
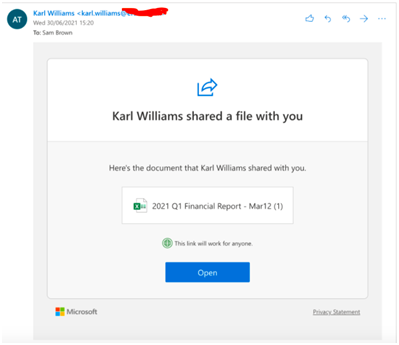
Here there could be two possibilities, either the user might be waiting for this or a similar report or you may suspect or doubt this email might have been sent erroneously, but curious to know & take a look into this. When the user tries to open this, he/she will be presented with the following screen :
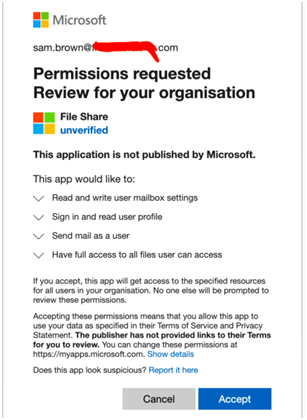
For a user, it would appear genuine as it carries all disclaimers. The user shall go for the “Yes give me access” prompt because the user has clicked through a thousand times as it’s a microsoftonline.com domain, it’s HTTPS and there’s a green tick in the corner so everything looks fine.
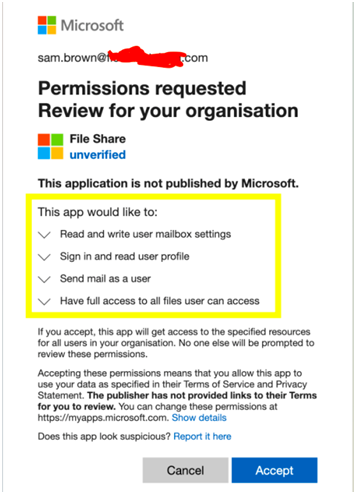
Points to Note
The user has given almost all the permission. These permissions allow the attackers to read and write any files you have access to – they could download all these files and then delete them. The attackers also got permission to send emails like you. They could send emails to your colleagues from you and phish them too, this isn’t impersonation where the email just “looks” like it came from you, the email DID come from you. Lastly, the attackers asked for permission to manipulate your Outlook settings, with this they could set up a mail forwarding rule so that they get copies of all your emails forwarded to them directly without even having to log in. And all of this happens until you delete the underlying OAuth app.
In a blog post, Microsoft warns that these attacks are on the rise. One notable example of this comes from the SANS Institute. They reported in August of 2020 that they had fallen victim to one of these attacks. As part of the investigation, they produced a report with details on how the attackers managed to convince an employee to install a malicious Microsoft 365 add-in to gain access.
How to Prevent: The only foolproof method of preventing this kind of attack is to prevent users from granting access to third-party apps. This is terrible for users though, and you’ll be missing out on all the productivity benefits these apps can bring. A more balanced approach is to let users find and request apps, but have administrators approve the apps. More and more platforms (including Microsoft 365 and Slack) are offering built-in “admin consent” workflows to make getting a second pair of eyes on new apps even easier. You can also make it even easier for users by pre-approving widely used apps from trusted publishers and users won’t even notice there is new protection in place 99% of the time. Quite a few new-age companies have been trying to address this challenge of the emerging technique of “Consent Phishing” one of them is Push.
Compiled by: RED Team of Armantec, led by Shamsher Bahadur – Cyber Security Practice Head.
This Article has been Submitted by Armantec Systems Pvt Ltd (www.armantecsystems.com), a Noida Based Threat Intelligence & RED Teaming Consulting Firm, with the prime focus on custom Ransomware Attacks Solution for Critical Information Infrastructures (CIIs).



