Nokia has reportedly suffered a data breach, exposing a trove of sensitive information. Hackers, identified as IntelBroker and EnergyWeaponUser, claim to possess and sell Nokia’s proprietary data, including source code, SSH keys, RSA keys, Bitbucket credentials, and SMTP accounts. This data, allegedly obtained via a third-party contractor directly involved in Nokia’s internal development, includes critical credentials that could grant unauthorized access to Nokia’s systems.
The International Cyber Digest, a prominent cybersecurity news outlet, confirmed that the breach extends to Nokia’s 4G/5G product data and affects Vodafone Idea Limited (VIL), one of the largest telecom providers in India, with over 217 million subscribers. With access to this sensitive customer data, the breach potentially endangers critical infrastructure and telecommunications networks in India, raising concerns about national security and privacy.
Investment Scam Exposed: Enforcement Directorate Cracks Down on “Pig-Butchering” Fraud
A file tree, provided as evidence, indicates the extent of the data compromised in the breach. The incident underscores the risks associated with third-party contractors and the cascading effects a breach in a technology provider’s infrastructure could have on connected industries.
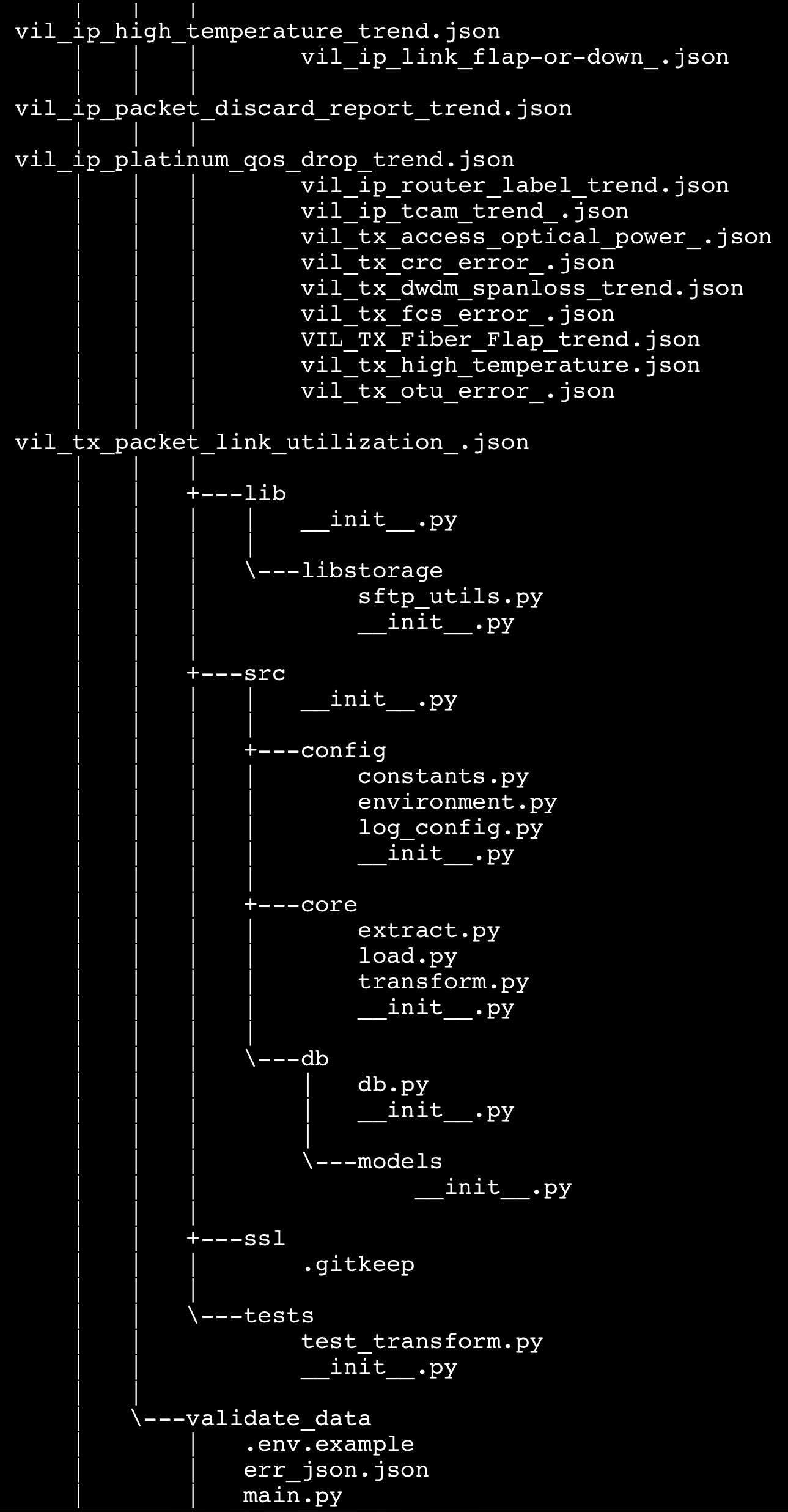
Experts warn that if these credentials and source codes are exploited, it could lead to large-scale disruptions or unauthorized access to sensitive telecom networks, impacting both consumer data and national telecom infrastructure. With telecommunications being integral to daily operations, such breaches highlight the need for enhanced cybersecurity protocols across all levels of development and data handling.
Nokia has yet to release an official statement regarding the breach, and further investigations are anticipated as the company assesses the damage and potential risks posed to its operations and partners.
This incident serves as a wake-up call for organizations to revisit their third-party risk management strategies and ensure that cybersecurity practices are rigorous enough to protect against insider threats and external attackers.
Follow The420.in on
Telegram, Facebook, Twitter, LinkedIn, Instagram and YouTube


