A sophisticated Chinese state-sponsored threat actor, dubbed Salt Typhoon, has infiltrated major U.S. telecommunications companies, maintaining access to their networks for over three years in some cases, Cisco has confirmed. The hackers leveraged a known security vulnerability and stolen login credentials to conduct their long-term espionage campaign.
Years of Persistent Access
Cisco Talos, the company’s threat intelligence arm, revealed that Salt Typhoon exploited a security flaw tracked as CVE-2018-0171 and obtained legitimate victim login credentials to gain initial access. The group then demonstrated an ability to persist within target environments, often across equipment from multiple vendors, for extended durations. In one instance, they maintained access for over three years. Talos described the hackers as highly sophisticated and well-funded, noting the “long timeline of this campaign” as evidence of “a high degree of coordination, planning, and patience — standard hallmarks of advanced persistent threat (APT) and state-sponsored actors.”
ALSO READ: Join Webinar on “Online Child Safety: Threats & Protection”
Stolen Credentials and Network Manipulation
While the exact method of obtaining the victim credentials remains unknown, Cisco confirmed that stolen credentials played a crucial role in the initial breach. The threat actor also attempted to acquire credentials through network device configurations and by deciphering local accounts with weak passwords. Furthermore, Salt Typhoon captured network traffic, including SNMP, TACACS, and RADIUS data, to gather additional credentials for future use. This traffic capture included the secret keys used between network devices and TACACS/RADIUS servers.
Living Off the Land and Obfuscation Techniques
Salt Typhoon employed “living-off-the-land” (LOTL) techniques, using the compromised trusted infrastructure as pivot points to move between different telecom networks. These compromised devices likely served as intermediate relays to reach final targets or as a first step for data exfiltration, allowing the adversary to remain undetected for extended periods.
ALSO READ: Ex-Meta Employee Sues After 15 Years: Alleges Sexual Harassment, Discrimination & Unfair Layoff
The hackers also modified network configurations to create local accounts, enable Guest Shell access, and facilitate remote access via SSH. They utilized a custom-built utility called JumbledPath to execute packet captures on remote Cisco devices through a jump-host defined by the attackers. JumbledPath, a Go-based ELF binary, can clear logs and disable logging to hinder forensic analysis and obfuscate malicious activity. Salt Typhoon also periodically erased relevant logs, including .bash_history, auth.log, lastlog, wtmp, and btmp, where applicable.
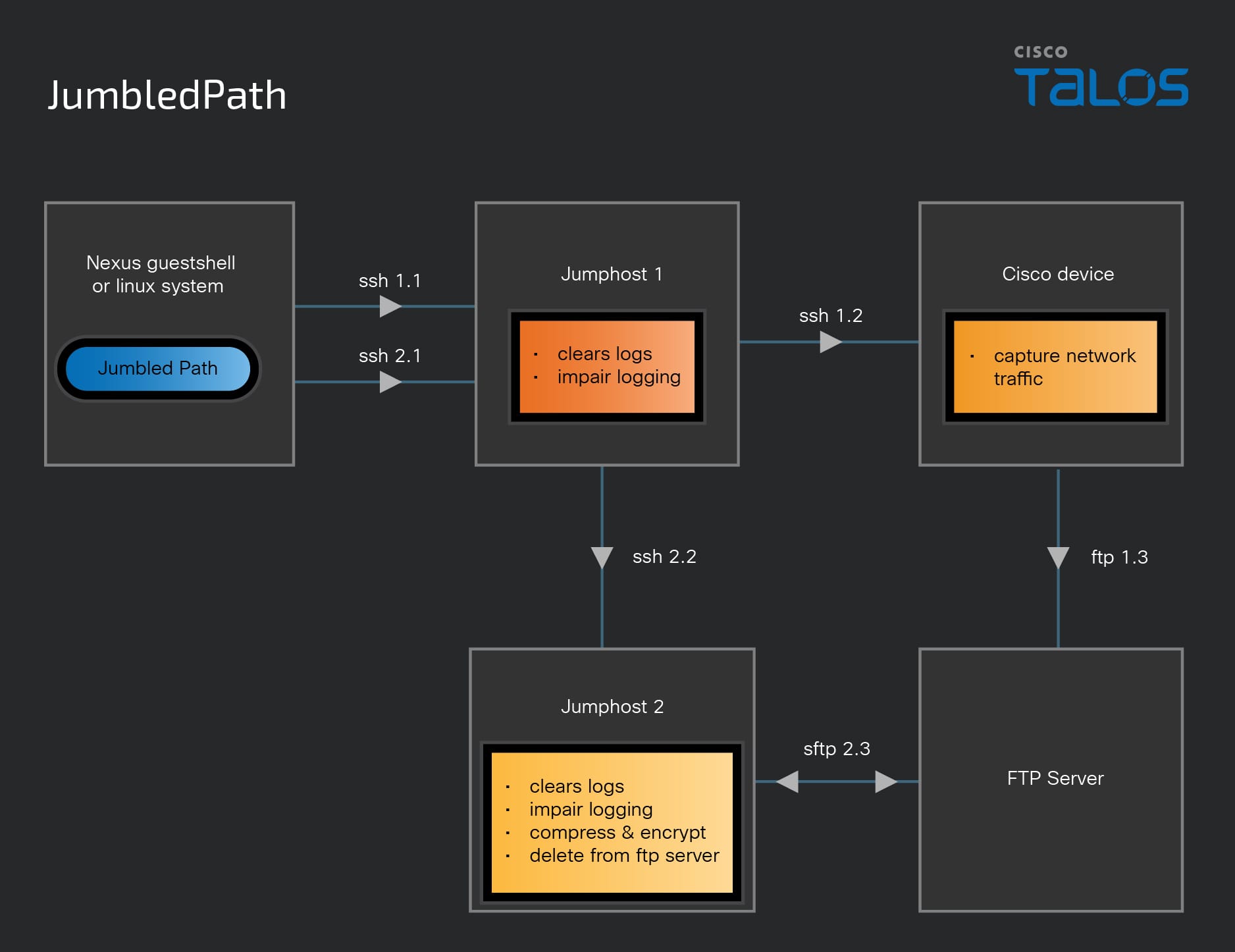
Cisco explained that JumbledPath helped to mask the original source and destination of requests, enabling the attackers to move through potentially non-publicly reachable devices or infrastructure. The threat actor repeatedly modified the loopback interface address on compromised switches and used that interface as the source of SSH connections to other devices within the target environment, effectively bypassing access control lists (ACLs).
Other Targeting of Cisco Devices
In addition to Salt Typhoon’s activities, Cisco identified separate, “pervasive targeting” of Cisco devices with exposed Smart Install (SMI), followed by the exploitation of CVE-2018-0171. This activity, however, is unrelated to Salt Typhoon and shows no overlap with any known threat actor or group. Cisco clarified that, contrary to some reports, they found no evidence that Salt Typhoon exploited other security bugs, such as CVE-2023-20198 and CVE-2023-20273, to infiltrate networks.


