New and advanced forms of cybersecurity threats that utilize multiple attack vectors continually emerge to target enterprises. In this environment, rapid evidence capture and response is key to quickly patching exploits and preventing another attack. Analysts need a dynamic solution that offers complete visibility of servers, critical systems, and endpoints, and enables them to proactively hunt for and respond to threats.
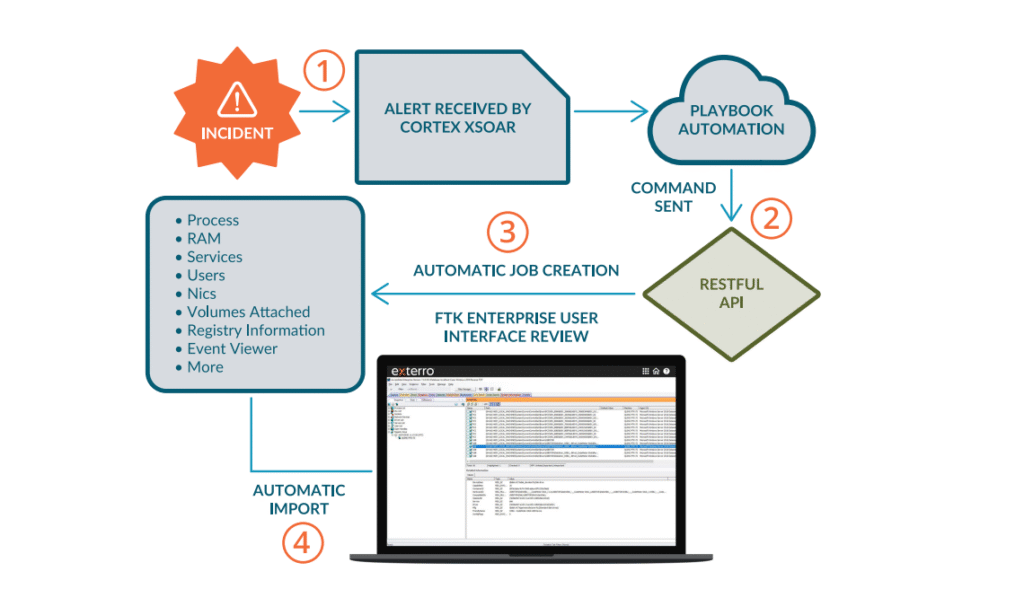
With the integration between the Palo Alto Networks Cortex XSOAR platform and the Exterro FTK Connect automation platform, users can now leverage Cortex XSOARs security orchestration and automation capabilities to trigger the immediate capture and preservation of endpoint evidence by FTK Enterprise, FTK Central, or FTK Lab, crucial for incident investigation and recovery.
FTK Connect can receive alerts from Cortex XSOAR and instruct FTK tools to automatically perform specific jobs on the endpoint that is generating the alert. For example, when Cortex XSOAR receives an alert, it sends a command through the FTK Connect API, which initiates an FTK Enterprise collection or remediation job on the endpoint, via the FTK remote agent. This saves time during all stages of incident response from triage and investigation to postanalysis and full recovery by preserving rich forensic data related to the root cause of the breach.
Preservation and the ability to provide defensible, verifiable evidence of how a breach occurred is critically important for adhering to regulatory standards, insurance requirements, and demonstrating compliance.
Features:
- Initiate the immediate collection of data at the designated endpoint with automated commands, or through the creation of incident playbooks
- Ensure evidence is collected and preserved in a legally defensible manner for full data integrity with forensically sound collection capabilities using a single, secure back-end database.
- Leverage the largest SOAR ecosystem of product integrations with Cortex XSOAR to enrich Exterro’s suite of post-breach analysis and response solutions.
Secure, Scalable, And Cost-Effective Investigations At Mazars
Benefits:
- Automatic preservation of electronic evidence
- Reduced risk with seamless handoff from incident detection to analysis and response
- Automate menial tasks, time-intensive processes, and investigative workflows
Product Compatibility:
- Cortex XSOAR Enterprise,
- FTK Enterprise, FTK Central, FTK Lab, and FTK Connect
USE CASE
#1 Automated Process List Upon Detection of Data Exfiltration
Challenge: Data exfiltration, or any unauthorized movement of data, is a very real threat for organizations. This type of data breach can happen at any time of day or night, so a SOC must be able to react immediately to preserve evidence related to the root cause of the breach, once it’s been detected. The key is to reduce data movement between platforms to avoid potential data spoliation.
Solution: Once potential data exfiltration is identified from inside the network, Cortex XSOAR receives the alert and can automatically trigger the FTK Connect restful API to instantly capture a complete process list. The process list identifies all processes currently running on the suspected machine, and their associated DLL files. From here, you can identify any processes that are unauthorized, and invoke FTK Enterprise to automatically remediate them. An automatic job collection is then initiated by FTK Enterprise at this specified endpoint. The Cortex XSOAR and Exterro integration automates this time-intensive process that would normally need to be completed manually.
Benefit: Exterro’s seamless integration with Cortex XSOAR reduces risk and speeds up an investigation once an internal breach is detected, with 24/7 real-time evidence collection and auditable preservation capabilities.
The Next Generation Of Digital Forensics — An Exterro Quick Guide
USE CASE
#2 Automated Memory Dump Upon Detection of Increased Network Traffic
Challenge: If you need to access an employee’s machine to investigate a possible breach, acquiring a memory dump is key to your investigation. A memory dump and/or a scan of the entire drive needs to happen immediately, which could occur during off hours, or in another time zone if your company is global.
Solution: After an internal incident is detected, Cortex XSOAR receives the alert and sends a command to FTK Connect to initiate collection of a memory dump. Once the memory dump is collected, you can proceed with the investigation and recovery of saved passwords, open network connections, or recover an entire webpage, which may only be stored in memory such as a page viewed in Chrome Incognito.
Benefit: By automating a memory dump from a compromised endpoint, the analysis can take place without alerting the suspecting individual, i.e. covert acquisition. When you collect a disk image after the incident has occurred, an investigator may be unable to analyze information cached in memory, depending on the actions of the endpoint user.




