In recent developments, law enforcement agencies have uncovered a sophisticated method used by cybercriminals to carry out a range of illegal activities, including fraud, cybercrime, and money laundering. Central to these operations is the use of SIM Boxes—telecommunication devices that allow criminals to exploit multiple SIM cards for sending bulk SMS messages, terminating international calls, and engaging in other illicit activities. This article by Rushi Mehta, a cyber expert, delves into the workings of SIM boxes, their illegal applications, and the investigative steps taken by authorities to combat this growing threat.
1. What is a SIM Box?
A SIM Box, or SIM Bank, is a telecommunications device that houses multiple SIM cards, enabling it to perform a variety of calling and messaging tasks. Typically utilized by criminal organizations, SIM Boxes are often employed in illegal activities such as sending bulk fraudulent SMS messages, cybercrime, terrorism, money laundering, and drug trafficking. The example provided is a SIM Box produced by Mootek Technologies in Chennai.

ALSO READ: Join The Movement: Registration Open for ‘Cyber Safe Uttar Pradesh’ Event by FCRF on October 17
2. How Does a SIM Box Work?
A standard SIM Box consists of the following components:
- Broadband/Internet Connection: Essential for terminating internet-based calls.
- SIM Box Management Software: This software facilitates the bulk sending of SMS messages through a computer interface and also allows for configuring the SIM Box. Some SIM Boxes also permit IMEI programming or alteration.
- SIM Card Slots: Where the SIM cards are inserted to enable operations.
3. Illegal Use of SIM Boxes
- International Calls: One of the primary illegal uses of a SIM Box is to bypass international call termination fees. SIM Boxes convert international calls into local calls, thereby avoiding the costs associated with international call termination. The process is typically as follows:

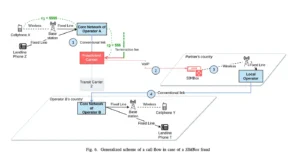
- An international call made over the internet is converted into a 2G/GSM call using a SIM Box.
- Bulk SMS: SIM Boxes are also used to send large volumes of fraudulent SMS messages. For example, a SIM Box with 512 SIM slots can automatically dispatch hundreds of thousands of fraudulent messages.
4. Investigation Process
Step 1: Obtain Call Detail Records (CDR)
When a victim reports receiving a suspicious call or SMS, the first step is to obtain the Call Detail Records (CDR) of the phone number in question. The following patterns are often indicative of SIM Box usage:
- No incoming calls, only continuous outgoing calls.
- No incoming SMS, only continuous outgoing SMS.
- SIM card remains in the same location for extended periods.
- SIM card registered with fake or fake KYC details.
- Multiple IMEI changes, often to feature phone IMEIs or random ones.
- Once it is established that a SIM Box has been used in the crime, law enforcement can deploy a team to locate the device.
Challenge: Accurately locating the SIM Box can be difficult if the location data is not precise. Alternative methods, which are not disclosed in public, may be used to pinpoint the SIM Box’s location.
Step 2: Broadband Connection
Since international call termination via SIM Box requires a broadband connection, investigators should obtain information and access logs from the broadband service provider during a raid.
Step 3: Legal Action
Law enforcement agencies can file charges under several legal frameworks, including the BNSS, the Indian Telegraph Act of 1885, and the Indian Wireless Telegraphy Act of 1933.
5. Recent Cases and Regulatory Actions
- Odisha : https://youtu.be/YMpnUy0y7so
- Pune : Pune ATS busts illegal telephone exchange in Kondhwa, seizes 7 SIM boxes and 3,788 SIM cards


What Can Telecom Operators Do?
Telecom operators can adopt solutions such as SMS firewalls or pattern detection algorithms to proactively identify SIM boxes within their networks. Once detected, they should promptly inform local law enforcement agencies.
Follow The420.in on
Telegram, Facebook, Twitter, LinkedIn, Instagram and YouTube




