Yes, hackers are using Microsoft’s professional networking site LinkedIn to spread malware which steals data by sending connection requests that appear to be from individuals employed by reputable companies.
This development has been confirmed by researchers from AI-powered cyber-security start-up CloudSEK.
The study claimed that scammers are sending links and files containing stealth malware using LinkedIn’s chat and job posting tools.
ALSO READ: Phishing Attack On Bank Customers Using SMS Apps, Warn Cyber Experts At CloudSEK
Hackers And LinkedIn ‘Connection’
Much of the trouble in this scenario lies in the fact that the hackers are able to build contacts on LinkedIn in a short span of time.
This fast speed of work is also in a way because of low-risk assessment by LinkedIn users when accepting new connections.
The alert by CloudSEK warns that on LinkedIn, “scammers can quickly build contacts and a reputation because the “majority of users accept every connection request they receive.”
Once they have the victims’ trust, the threat actors spread malicious files and links, which the victims click on without a second thought.
A stealer malware is installed on the victim’s computer after the email has been opened, where it gathers sensitive information like passwords, credit card numbers, and other details before sending it to the threat actors.
ALSO READ: Job Scam: Middle East New Target Of Phishing Scams, Cyber Thugs Pose As UAE Ministry Officials
This widespread abuse of LinkedIn may represent the greatest danger to date, according to CloudSEK.
“The underlying promise of professionalism makes it easier for scammers to run campaigns at scale,” says Rahul Sasi, CEO and Founder of CloudSEK.
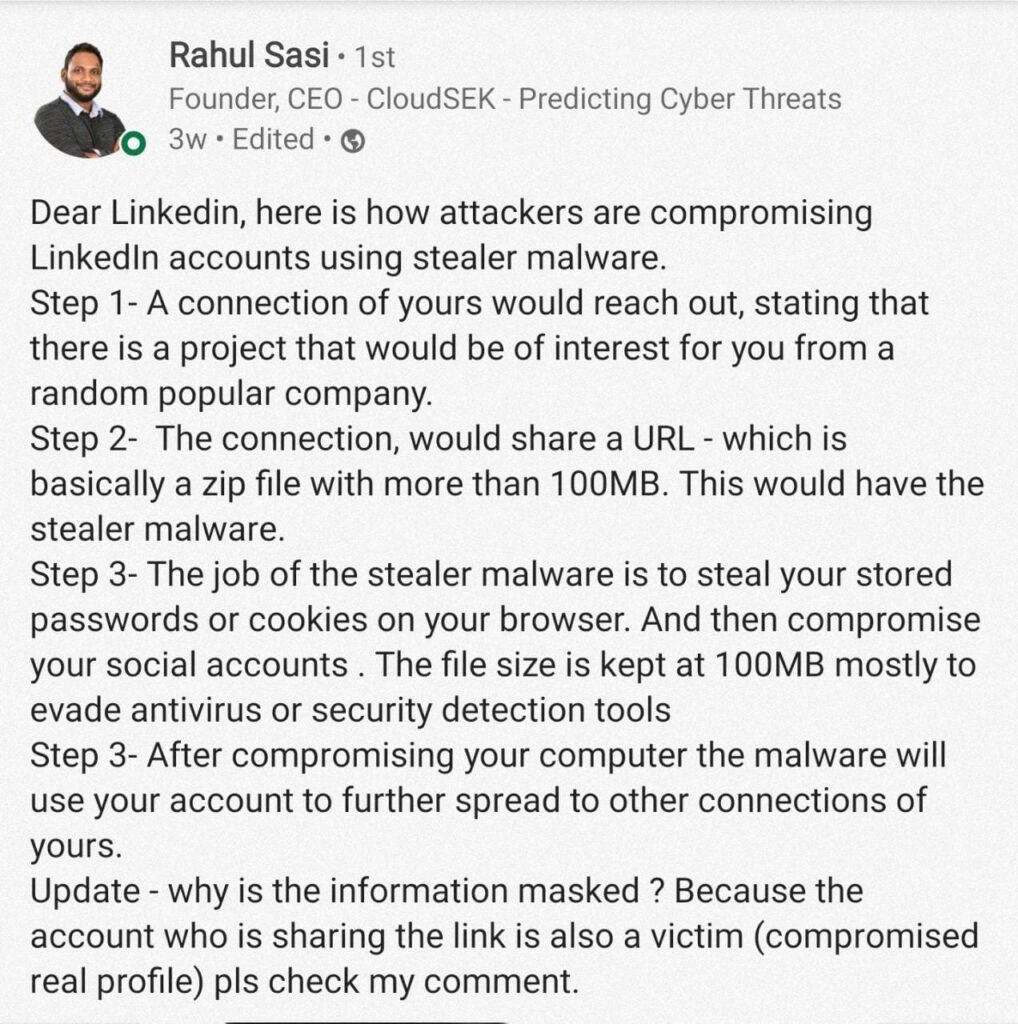
How The Malware Works?
A LinkedIn connection contacts you about a project from a reputable company that they think you might be interested in.
The information thief is embedded in a zip file or URL that the connection shares. To get around antivirus and security software, the file size is typically limited to 100MB.
The stealer malware is automatically downloaded onto your system once the file is opened. Passwords and cookies kept on your browser are then stolen, according to the report.

The victim’s social media and email accounts are then compromised and hijacked using the stolen credentials. The scam doesn’t end here, now using the victim’s credentials people in his/her connection are targeted.
Even if the requester is connected to someone you know, Sasi advised all users to confirm connection requests before accepting them. Before opening any documents or files shared on LinkedIn, it’s a good idea to scan them.
Follow The420.in on
Telegram | Facebook | Twitter | LinkedIn | Instagram | YouTube



