NOIDA: “Bad Actors” are earning a good amount of money using techniques like Ransomware, Financial Data Breaches, ATM fraud, Cyber extortions, etc. Estimated global losses from cybercrime are over $1 trillion for 2020. This enormous amount of money is scattered into various money deposits in the form of breached credit and debit cards, crypto wallets, breached bank accounts, and even hard cash extracted from multiple ATMs.
The Biggest Problem for “Bad Boys”
The money collected from various sources is “DIRTY,” i.e., very easily trackable by law enforcement agencies. For example:
1. Money collected from ATM hacks can be traceable based on currency numbers, so they usually cannot be deposited into any other bank or directly convert into digital currency without triggering any alarm.
2. Digital currency payment, received from Ransomware or any other digital extortions, can be traced back to its sources using “crypto sinkhole” techniques.
3. Exposed financial data (i.e., breached debit and credit cards) cannot be used directly to transfer money to the Bad Boy’s account.
From the above analysis, this gives a sense that we are secure, and whatever the hackers will do, we can trace them back and recover our stolen money. Well, it is NOT the scenario. Had this been true, Commercial Attacks would not had taken place. Earlier hackers use to implement some form of financial anonymity using techniques like :
1. Crypto Tumbler – A unique technique used to make Bitcoin and any other cryptocurrency, collected from attacks like Ransomware, semi-anonymous and tough to execute crypto forensic analysis. (Will discuss in detail in an upcoming post)
2. Carding – Previously, hackers use to sell bulk stolen debit and credit cards for a minimum price, all having balance ranges from $200-$800 for a minimum fee of $50-$80.
Is This Enough?
For a couple of years, these techniques saved hackers from getting caught. Still, sophisticated crypto forensic analysis techniques and enhanced security posture, and cyber awareness of almost all banks made these techniques very tough and not financially viable for Bad Boys.
Latest Technique used by Bad Boys.
Because of the above-stated issues, a new way of money laundering emerges with enhanced security and protection for hackers. As a result, the new technique successfully converts “Dirty” traceable money into “White” money with a proper transaction trail. On. The basis of our Analysis, we have identified this new technique called “EasyMoney.”
“EasyMoney” is a technique where a website is created in *DARK web, where a regular user can go and deposit a small amount of money, and in return, receives a pretty large number of sums instantly. Though this Technique sounds not malicious at first, we will try to clear this concept below.
E.G
Let’s assume a hacker extorted $2 million from a ransomware attack. Now, this amount is with him in the form of cryptocurrency in various crypto wallets. If the entire amount needs to be encashed, that will trigger many alarms, and here “EasyMoney” technique comes in place.
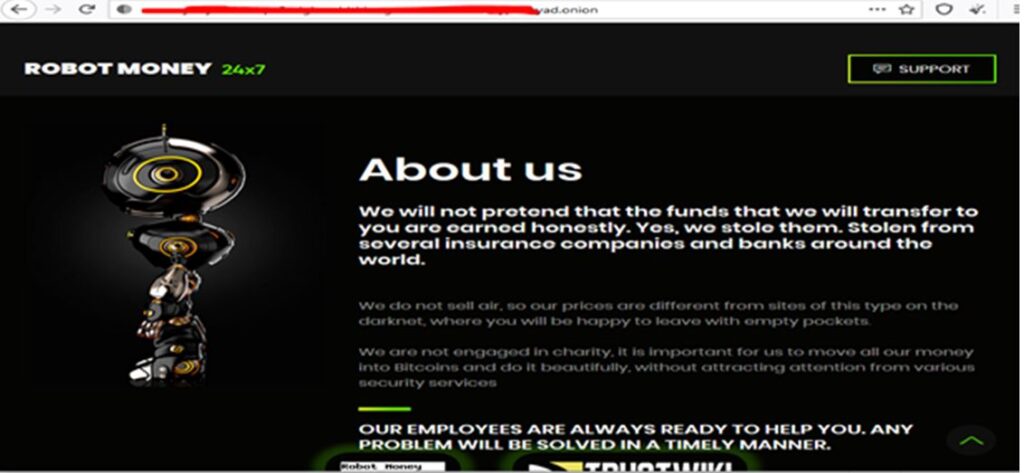
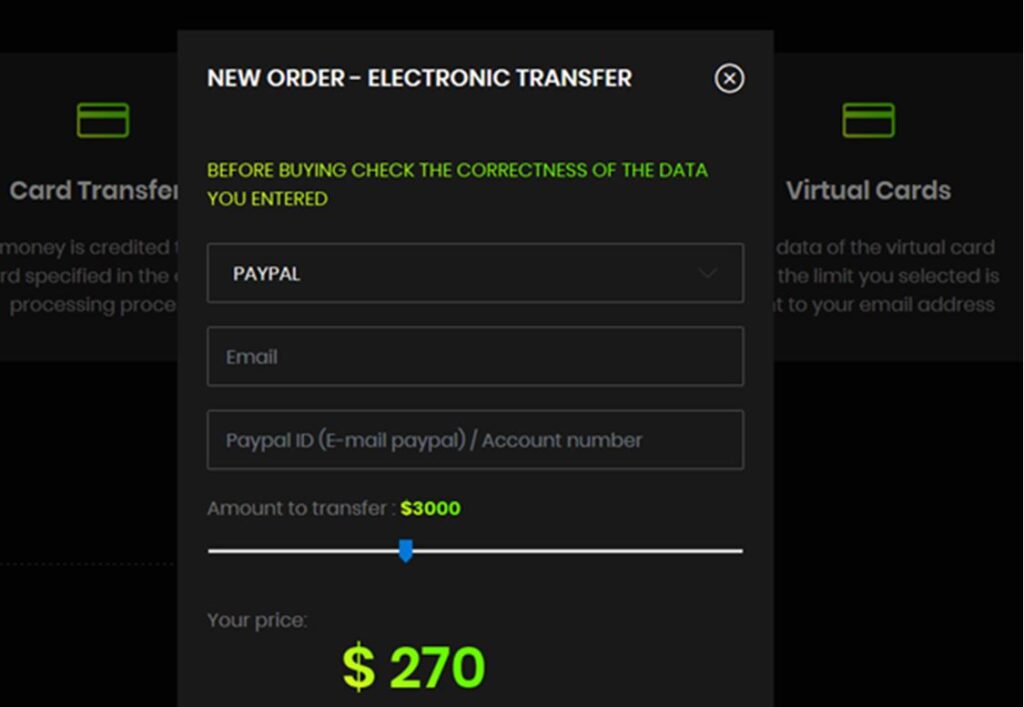
Here an average user can come and buy a large amount of money, using small fees. As seen in the above screenshot, a user pays only $270 and receives $3000. This money can be transferred to the user’s PAYPAL account, bitcoin wallet, and digital debit card. This way, hackers can convert 10%-30% of the “DIRTY” money into “White” cash, which will be untraceable and scattered worldwide. The Dark-Web provides the essential cover of anonymity.
This way, hackers are transferring millions of dollars. However, there are some other ways like this, using which anonymous money laundering is possible, which we shall be covering in our upcoming post.
Case Study by: RED Team of Armantec, led by Shamsher Bahadur – Cyber Security Practice Head.
This Article has been Submitted by Armantec Systems Pvt Ltd (www.armantecsystems.com), a Noida Based Threat Intelligence & RED TEAM Consulting Firm, with the prime focus on custom Ransomware Attacks Solution for Critical Information Infrastructures (CIIs).
Follow The420.in on Facebook, Twitter, LinkedIn, Instagram, YouTube & Telegram



