NEW DELHI: Hundreds of organizations using Atlassian products – Jira, Confluence, and BitBucket are at risk of cyber-attack. CloudSEK researchers found that for products like Jira, Confluence, and BitBucket cookies are not invalidated when the password is changed with 2FA (Two-factor Authentication) set, as the cookie validity is 30 days. They are valid until the user logs out or 30 days have passed.
Researchers at CloudSEK have discovered that threat actors can exploit this vulnerability to seize control of the Jira accounts of hundreds of businesses.
According to CloudSEK’s record, more than 1,282,859 hacked machines and 16,201 Jira cookies are for sale on dark web marketplaces. In the last 30 days, more than 2,937 hacked PCs and 246 Jira credentials have been made public. CloudSEK claims their team has detected at least one infected machine from a Fortune 1000 business in the past 90 days. This only takes their major domains into account, not their subsidiaries.
CloudSEK offers a free tool that allows businesses to determine if their compromised laptops and Jira accounts are being sold on the dark web.
With more than 10 million users across 180,000 businesses, including 83 percent of Fortune 500 organisations, Atlassian solutions are widely utilised worldwide. Furthermore, threat actors actively use this vulnerability to compromise enterprise Jira accounts.
Even if 2FA is implemented, stolen Atlassian cookies can lead to unauthorised account access.
ALSO READ: Phishing Attack On Bank Customers Using SMS Apps, Warn Cyber Experts At CloudSEK
Even if the password is reset and 2FA is activated, the cookies of Atlassian products stay valid for 30 days, according to an analysis by CloudSEK. Consequently, threat actors can recover Jira, Confluence, Trello, or BitBucket sessions using stolen cookies, even without access to Multi-factor Authentication (MFA), OTP/ PIN. By default, cookies expire when the user signs out or after 30 days.
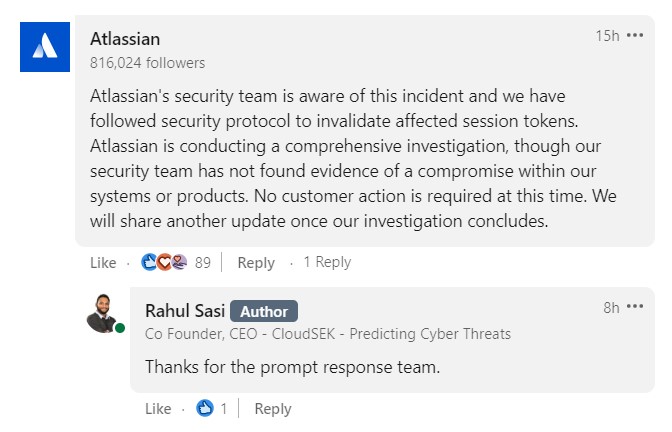
In a statement, Atlassian said its security team “is aware of this incident and we have followed security protocol to invalidate affected session tokens. Atlassian is conducting a comprehensive investigation, though our security team has not found evidence of a compromise within our systems or products. No customer action is required at this time. We will update our customers once our investigation concludes.”
ALSO READ: Job Scam: Middle East New Target Of Phishing Scams, Cyber Thugs Pose As UAE Ministry Officials
More than 200 unique instances of atlassian.net-related credentials/cookies have been offered for sale on dark web marketplaces in the past 30 days. Given that the credentials were offered for sale within the past 30 days, it is likely that the majority of them are still valid.
CloudSEK reports that Atlassian is aware of the issue and working to resolve it.
The vulnerability is a known issue, according to the researchers. However, the majority of businesses are more concerned with eliminating other website vulnerabilities, such as cross-site scripting, which allow attackers to obtain security tokens and session cookies.
MITIGATION
To mitigate the vulnerability, CloukSEK recommends that administrators of IT and security:
- Encourage employees to log out of sensitive applications periodically.
- Configure a shorter idle session for Atlassian products via the Security Authentication policies area of admin.atlassian.com until Atlassian provides a remedy.
- Implement idle-session timeout to require re-logins.
- Watch cybercrime forums for the most recent threat actor strategies.
Follow The420.in on
Telegram | Facebook | Twitter | LinkedIn | Instagram | YouTube



