In today’s world where COVID-19 is spreading rapidly, people are getting affected with the virus and are splurging humongous amounts of money on medication and hospital treatment. Now, to keep businesses running, the ‘New Normal’ for people all over the world is Work from Home known as ‘WFH’ which is something all sectors have adopted as a policy for their employees.
As the number of work from home employees is continuously increasing, hackers are taking undue advantage of it, creating and conducting specially crafted malware, phishing attacks and viruses for work from home employees, such as to lure them into clicking on the links and syphoning out a lot of money.
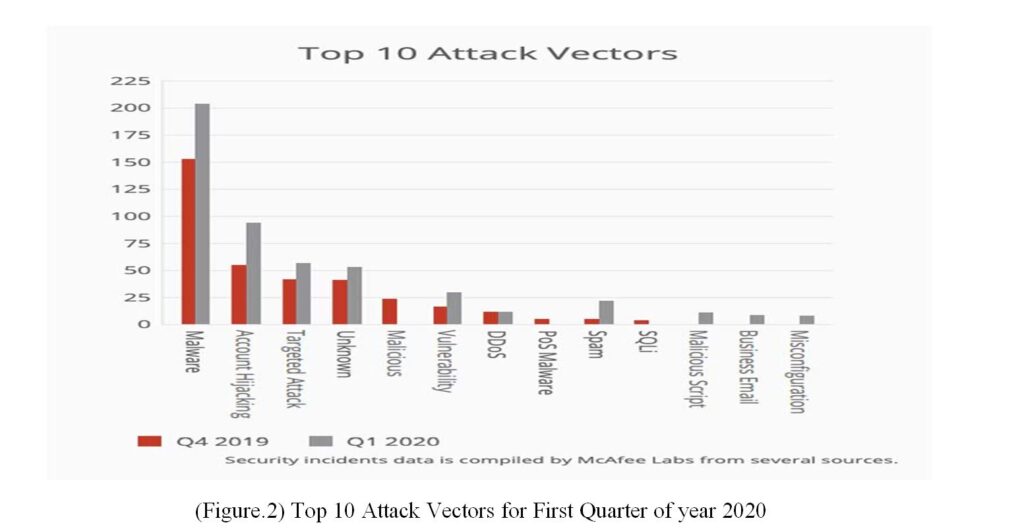
While COVID-19 is increasing, virtual viruses are also increasing.
To put things into perspective, I would like to explain to you the parallel between COVID-19 and the latest hacking attempts.
As a person gets affected by COVID-19, the initial symptoms show up only after 14 days. After 14 days, depending on the person’s immunity, symptoms start to grow, some of them being: coughing, breathing issues, fever, body ache, etc.
Now similarly, once a hacker attacks the system, it takes up to 10 to 14 days – depending on the severity of the attack – to reveal the damage. After some days, the computer starts showing symptoms such as a reduction in the speed at which it performs tasks, a constant crashing of applications, the automatic locking of the screen, etc. caused due to the virus or malware present in your computer.
Now let’s see how COVID-19 gets injected into a person and how a virus gets injected into your computer system.
The chain of COVID-19 starts when you are nearby a COVID-19 affected person or entering confined spaces, such as wards managed by hospitals for COVID-19 patients, without wearing a mask and due to improper sanitization. At such times, the virus may enter your body through the throat, mouth or nose. The virus can also live up to 3 hours in the air, so you could breathe in the virus from the air in a room where an infected person breathed, coughed or sneezed within that period.
Similarly, a virus enters your computer through many different ways unknown to you. For example; in close Bluetooth proximity unknown files can get shared, data can get injected into your computer through USB if you click on spam emails or phishing emails which have links attached, if you are connected to a public Wi-Fi network which can be intercepted easily by the hacker, then the virus can start entering your system and slowly execute itself in the background via some commands or processes after which it can even spread into to your company infrastructure.

When does it start to develop?
In the case of COVID-19, the virus develops in your body because of weak immunity and starts changing the bodily parameters. It enters due to the absence of antibodies and starts spreading, impacting the different organs and its functions which in turn gives rise to symptoms such as dizziness, lower oxygen level, constant weakness, loss of smell or taste, etc.
In case of a computer virus, it starts developing in your system because of plugging in a USB device without scanning it, unwanted Bluetooth file sharing, surfing through suspicious websites which download malicious files in the background, and also due to no pre-installed antivirus software in the system to detect and diagnose it.
What happens after the development?
As COVID-19 develops in the human body, it hijacks healthy cells and takes over them. Eventually, it kills some of the healthy cells. For instance, your lungs might become inflamed making it tough for you to breathe, your liver might get affected and not work at its optimum, etc.
Once the hacker has successfully gained access to your system, they start to escalate their privileges to the administrative user using some local exploitative methods. The hacker soon gets access to your administrator account and now has full control over your computer such as changing some in-built antivirus policies, gathering sensitive information, confidential documents, resetting your computer password, and the likes. Replication occurs when the virus has been loaded into memory and has access to CPU cycles. File infection relies on the virus’s ability to attach itself to a file that provides access to CPU cycles. Self-mutation is a technique used by virus writers to make their viruses more difficult to detect by antivirus software.
How to recover from these attacks?
After testing positive for COVID-19, a person is quarantined for the next 14 days so that they cannot infect anyone in the vicinity. During this period, antibodies will get developed in the person’s body and will help them recover. Doctors also try to treat critical patients with ways such as putting them on a ventilator, oxygen support, antibiotics, etc. to boost their immunity.
Installing Microsoft Outlook ATP (Advanced Threat Protection) can help detect phishing emails or spam emails and also links attached to them, and aid in further dividing them into separate folders for more investigation and verification of legitimacy. In case of a virus, install antivirus software’s which will detect the virus at its entry point. Install EDR which will do the additional steps of blocking and remediating malicious artefacts or behaviors that are detected. Install DLP to know when a data leak is taking place from the network. Website access can be dropped by using a web application proxy server. Also, Identity and Access Management (IAM) looks after the cases in which the individuals will be granted or denied special privileges. It provides each employee with their own unique digital identity. This unique identity should be established using Identification, Authentication and Authorization.
What are the preventive measures?
The government is pushing guidelines for continuous use of masks, sanitizers and social distancing. It is also emphasizing on the fact that one must step out of their homes only in extreme cases or else stay home. If you are facing any symptoms of COVID-19, reach out to doctors or hospitals for immediate action and proper treatment.
COVID-19 is a completely new virus and so is the Zero-Day virus – a mutation of the same – found in some people. Vaccines are coming up but none of them assures the full removal of mutated COVID-19 from the human body.
In the case of cyber security, add some tools like VIRUS Total to identify the legitimacy of a file, website, URL, etc. For non-familiar IP addresses, use websites like Abused IP DB to check the information of the IP address. Also, install anti-virus software’s and update them regularly. Before opening any file or link ensure that links are not suspicious, files are clean and do not contain any hidden virus. Also ensure that your employees are attending different types of training courses such as VAPT, Red Teaming, and Forensics etc. to ensure that they are aware of the threats. Make sure USB ports are blocked. If a USB is detected make sure the anti-virus is throwing an alert. Make sure your Bluetooth is blocked across all devices. Monitor the network traffic and check for any suspicious activity. Using IPS (Intrusion Prevention System) to analyze the packets and identify its legitimacy will reject or accept the packet and will stop malicious traffic from reaching your network. Use IDS (Intrusion Detection System) so that it detects and stops the hacker’s attacks based on some signatures and comparison between the inbound traffic.

The Writer: Pranav Bapat is a consultant – SOC Team, SLK Global Solution, Pune.
Email: pbapat96@gmail.com



